- Fix Windows Update errors by using the DISM or System Update Readiness tool
- Symptom
- Resolution for Windows 8.1, Windows 10 and Windows Server 2012 R2
- Resolution for Windows 7 Service Pack 1 (SP1) and Windows Server 2008 R2 SP1
- Resolution — Download the package from Microsoft Update Catalog directly
- Description of the common corruption errors
- What does the System Update Readiness tool do
- Verify the integrity of resources
- Logging
- How to fix errors that are found in the CheckSUR log file
- MSE Definitions/Signatures Update FAQ
Fix Windows Update errors by using the DISM or System Update Readiness tool
Original product version: В Windows 10, version 1809 and later versions, Windows 8.1, Windows Server 2012 R2, Windows 7 Service Pack 1, Windows Server 2008 R2 Service Pack 1
Original KB number: В 947821
Symptom
Windows updates and service packs may fail to install if there are corruption errors. For example, an update might not install if a system file is damaged. The DISM or System Update Readiness tool may help you to fix some Windows corruption errors.
This article is intended for Support agents and IT professionals. If you are home users and looking for more information about fixing Windows update errors, see Fix Windows Update errors.
Resolution for Windows 8.1, Windows 10 and Windows Server 2012 R2
To resolve this problem, use the inbox Deployment Image Servicing and Management (DISM) tool. Then, install the Windows update or service pack again.
Open an elevated command prompt. To do this, open Start menu or Start screen, type Command Prompt, right-select Command Prompt, and then select Run as administrator. If you are prompted for an administrator password or for a confirmation, type the password, or select Allow.
Type the following command, and then press Enter. It may take several minutes for the command operation to be completed.
When you run this command, DISM uses Windows Update to provide the files that are required to fix corruptions. However, if your Windows Update client is already broken, use a running Windows installation as the repair source, or use a Windows side-by-side folder from a network share or from a removable media, such as the Windows DVD, as the source of the files. To do this, run the following command instead:
Replace the C:\RepairSource\Windows placeholder with the location of your repair source. For more information about using the DISM tool to repair Windows, reference Repair a Windows Image.
Type the sfc /scannow command and press Enter. It may take several minutes for the command operation to be completed.
Close the command prompt, and then run Windows Update again.
DISM creates a log file (%windir%/Logs/CBS/CBS.log) that captures any issues that the tool found or fixed. %windir% is the folder in which Windows is installed. For example, the %windir% folder is C:\Windows.
Resolution for Windows 7 Service Pack 1 (SP1) and Windows Server 2008 R2 SP1
To resolve this problem, use the System Update Readiness tool. Then, install the Windows update or service pack again.
Download the System Update Readiness tool.
select the download link in the following table that corresponds to the version of Windows that is running on your computer. For more information about how to find the version of Windows that you installed, see Find out if your computer is running the 32-bit or 64-bit version of Windows.
This tool is updated regularly, we recommend that you always download the latest version. This tool is not available in every supported language. Check the link below to see if it is available in your language.
| Operating system | Download link |
|---|---|
| x86-based (32-bit) versions of Windows 7 SP1 | Download the package now. |
| x64-based (64-bit) versions of Windows 7 SP1 | Download the package now. |
| x64-based (64-bit) versions of Windows Server 2008 R2 SP1 | Download the package now. |
| Itanium-based versions of Windows Server 2008 R2 SP1 | Download the package now. |
Install and run the tool.
Select Download on the Download Center webpage, then do one of the following:
- To install the tool immediately, select Open or Run, and then follow the instructions on your screen.
- To install the tool later, select Save, and then download the installation file to your computer. When you’re ready to install the tool, double-select the file.
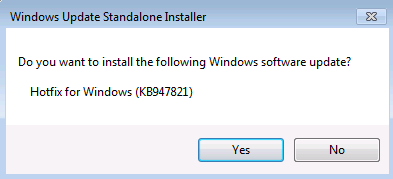
In the Windows Update Standalone Installer dialog box, select Yes.
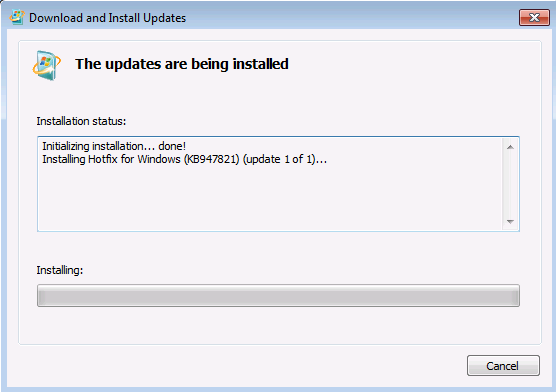
When the tool is being installed, it automatically runs. Although it typically takes less than 15 minutes to run, it might take much longer on some computers. Even if the progress bar seems to stop, the scan is still running, so don’t select Cancel.
When you see Installation complete, select Close.
Reinstall the update or service pack you were trying to install previously.
To manually fix corruption errors that the tool detects but can’t be fixed, see How to fix errors that are found in the CheckSUR log file.
Resolution — Download the package from Microsoft Update Catalog directly
You can also try to directly download the update package from Microsoft Update Catalog, and then install the update package manually.
For example, you may have problems when you try to install updates from Windows Update. In this situation, you can download the update package and try to install the update manually. To do this, follow these steps:
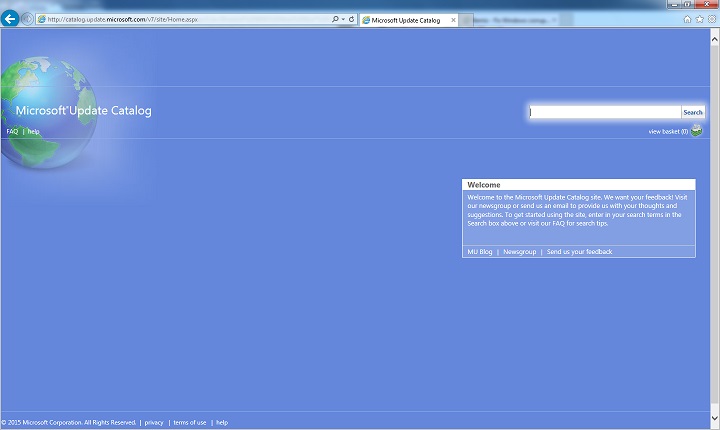
Open Microsoft Update Catalog in Internet Explorer.
In the search box, input the update number that you want to download. In this example, input 3006137. Then, select Search.
Find the update that applies to your operating system appropriately in the search results, and then select Add to add the update to your basket.
Select view basket to open your basket.
Select Download to download the update in your basket.
Select Browse to choose a location for the update you are downloading, and then select Continue.
Select Close after the download process is done. Then, you can find a folder that contains the update package in the location that you specified.
Open the folder, and then double-select the update package to install the update.
If the Windows update or service pack installed successfully, you are finished. If the problem is not fixed, or if System Update Readiness Tool cannot find the cause, contact us for more help.
Description of the common corruption errors
The following table lists the possible error code with Windows Update for your reference:
| Code | Error | Description |
|---|---|---|
| 0x80070002 | ERROR_FILE_NOT_FOUND | The system cannot find the file specified. |
| 0x8007000D | ERROR_INVALID_DATA | The data is invalid. |
| 0x800F081F | CBS_E_SOURCE_MISSING | The source for the package or file not found. |
| 0x80073712 | ERROR_SXS_COMPONENT_STORE_CORRUPT | The component store is in an inconsistent state. |
| 0x800736CC | ERROR_SXS_FILE_HASH_MISMATCH | A component’s file does not match the verification information present in the component manifest. |
| 0x800705B9 | ERROR_XML_PARSE_ERROR | Unable to parse the requested XML data. |
| 0x80070246 | ERROR_ILLEGAL_CHARACTER | An invalid character was encountered. |
| 0x8007370D | ERROR_SXS_IDENTITY_PARSE_ERROR | An identity string is malformed. |
| 0x8007370B | ERROR_SXS_INVALID_IDENTITY_ATTRIBUTE_NAME | The name of an attribute in an identity is not within the valid range. |
| 0x8007370A | ERROR_SXS_INVALID_IDENTITY_ATTRIBUTE_VALUE | The value of an attribute in an identity is not within the valid range. |
| 0x80070057 | ERROR_INVALID_PARAMETER | The parameter is incorrect. |
| 0x800B0100 | TRUST_E_NOSIGNATURE | No signature was present in the subject. |
| 0x80092003 | CRYPT_E_FILE_ERROR | An error occurred while Windows Update reads or writes to a file. |
| 0x800B0101 | CERT_E_EXPIRED | A required certificate is not within its validity period when verifying against the current system clock or the time stamp in the signed file. |
| 0x8007371B | ERROR_SXS_TRANSACTION_CLOSURE_INCOMPLETE | One or more required members of the transaction are not present. |
| 0x80070490 | ERROR_NOT_FOUND | Windows could not search for new updates. |
| 0x800f0984 | PSFX_E_MATCHING_BINARY_MISSING | Matching component directory exist but binary missing |
| 0x800f0986 | PSFX_E_APPLY_FORWARD_DELTA_FAILED | Applying forward delta failed |
| 0x800f0982 | PSFX_E_MATCHING_COMPONENT_NOT_FOUND | Can’t identify matching component for hydration |
What does the System Update Readiness tool do
Verify the integrity of resources
The System Update Readiness tool verifies the integrity of the following resources:
- Files that are located in the following directories:
- %SYSTEMROOT%\Servicing\Packages
- %SYSTEMROOT%\WinSxS\Manifests
- Registry data that is located under the following registry subkeys:
- HKEY_LOCAL_MACHINE\Components
- HKEY_LOCAL_MACHINE\Schema
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Component Based Servicing
This list may be updated at any time.
When the System Update Readiness tool detects incorrect manifests, Cabinets, or registry data, it may replace the incorrect data with a corrected version.
Logging
The System Update Readiness tool creates a log file that captures any issues that the tool found or fixed. The log file is located here:
How to fix errors that are found in the CheckSUR log file
To manually fix corruption errors that the System Update Readiness tool detects but can’t fix, follow these steps:
%SYSTEMROOT% is an environment variable that saves the folder in which Windows is installed. For example, generally the %SYSTEMROOT% folder is C:\Windows.
Identify the packages that the tool can’t fix. For example, you may find the following in the log file:
In this case, the package that is corrupted is KB958690.
Copy the package (.msu) to the %SYSTEMROOT%\CheckSUR\packages directory. By default, this directory doesn’t exist and you need to create the directory.
MSE Definitions/Signatures Update FAQ
The following is a description of the automatic updating process for Microsoft Security Essentials virus and spyware definitions.
MSE requires that the Automatic Update service be running and started, but it does not matter what you have selected in Control Panel/Automatic Updates for the way you want to handle critical and important updates for Windows. It is recommended, however, that you at least allow Automatic Updates to notify you about critical and important updates so that you can choose to download and install them as soon as possible and help keep your operating system secure with the latest patches from Microsoft.
(added 11/16/12) Windows Defender in Windows 8 requires Automatic Updates to be configured to download and install updates automatically or the Windows Defender signature updates will not install automatically.
(The following was true prior to build 1961/1963) You will not be offered MSE signature updates via Windows Automatic Updates automatically and they will not be offered if you go to Windows Updates manually to check for updates. MSE uses the «pipe» for Windows Update only.
Build 1961/3: Here’s what I know (perhaps I should say » think that I know «) right now about the relationship of MSE background automatic updates to Windows Automatic Updates.
MSE updates have changed slightly in the new release. Updates are*also* pushed through Windows Automatic Updates via the AU check and this *does* depend on your AU selection. If you have it set for install automatically, you may see signature updates multiple times per day. If you have it set to notify only, you may see the WU tray icon telling you about available updates. You can choose to ignore this and let MSE install the updates when it checks, or you can install based on the WU pending update notice.I believe that in some cases, the tray icon will sit there for a while and then MSE will do its check, install the update and the WU tray icon will go away.Depending on when AU checks for updates and when MSE checks for and installs updates, you may note random behavior with the notification.
I’m not 100% sure of the above, however, I believe that it is fairly close. I’m trying to get some clarification, but I do know that the intent of the AU/WU active notification and installation of updates is to provideanother channel for the signatures to be regularly updated.
MSE Updates are downloaded automatically using the AU «pipe» which includes BITS, the Background Intelligent Transfer Service. It must be running and up to date, or MSE updates may have a problem.
The Microsoft Antimalware group deploys updates for MSE (also Forefront and Windows Live OneCare) typically a few times daily. It is not critical for you to check for updates throughout the day because when MSE checks for updates, the offered updates will be downloaded and added to the database.
MSE will report that it is up to date and in good status even if the definitions are a few days old on the PC. Note that MSE uses the local signatures for common protection, but it also employs behavioral detection. If suspicious activity is detected, MSE will communicate with the servers to determine if a match has been reported and will immediately download any information needed to deal with the threat if a match is found.
Updates are a once per 24 hour check on a schedule determined by MSE. There is no setting within MSE to change the scheduled time or frequency.
Optionally, you can add a check for updates by setting check for updates before scan and setting up a scheduled scan daily (for a time when the PC will be on as it won’t run a missed scan later).
MSE will also check 10 minutes or so after boot or wake from sleep if there is a network connection *and* the current updates are greater than 24 hours old.
It will * not * perform this catch up check if the current definitions were installed within the past 24 hours, but will wait until the next scheduled check time.
** This «catch up» check is apparently not always working for people on wake from sleep/standby/hibernate. Microsoft is aware of this problem and are working to fix this in a future release. So, if the PC happens to be asleep when the scheduled check is supposed to happen, and you don’t have the extra check enabled, and you don’t reboot, you can have older definitions. In some cases, several days old.(Note that this appears to have been fixed in build 1961)
MSE will report that it is up to date until the signatures are greater than 7 days old. At that point, it will change the status to At Risk so that you can check for updates manually.
MSE will not update through an authenticated Proxy Server.
MSE can update using WSUS. This was changed to allow colleges and universities to make signature updates available on WSUS for students’ personal computers running MSE.
You can manually check for updates at any time, though this should not generally be needed. Open MSE, click on the Updates tab and click the button to check for updates.
You can manually download a full engine and definition package from the Microsoft Malware Protection Center and apply it to a PC running MSE without a clear network connection, if desired. The full package is quite large, about 40 megs. Typically, the automatic (or manual from within MSE) updates are a few megs in size.
We’ll update this FAQ as needed.
-steve
Microsoft MVP Windows Live
Windows Live OneCare| Live Mesh|MS Security Essentials Forums Moderator