- How to Run a Program as a Different User (RunAs) in Windows 10?
- How to Run an App as Different User from File Explorer?
- “Run As Different User” Option is Missing in Windows 10
- Using the RunAs Command to Run a Program as Another User from CMD
- How to Use RunAs Without Password Prompt?
- How to Create a Shortcut to Run As Different User?
- How to Run MMC Snap-Ins As a Different User?
- Add “Run As” Option to Start Menu in Windows 10
- Service User Accounts
- Run a process from a windows service as the current user
- 2 Answers 2
How to Run a Program as a Different User (RunAs) in Windows 10?
In all supported Windows versions it is possible to run applications on behalf of another user (Run As) in the current session. This allows you to run a script (.bat, .cmd, .vbs, .ps1), an executable (.exe) or an application installation (.msi, .cab) with another user (usually elevated) privileges.
For example, you can use the RunAs to install apps or run MMC snap-ins under the administrator account in an unprivileged user session. The opportunity to run a program as a different user may be useful when an application is configured under another user (and stores its settings in another user’s profile, which the current user cannot access), but it must be started with the same settings in another user’s session.
In Windows 10 there are several ways to run a program/process on behalf of another user.
How to Run an App as Different User from File Explorer?
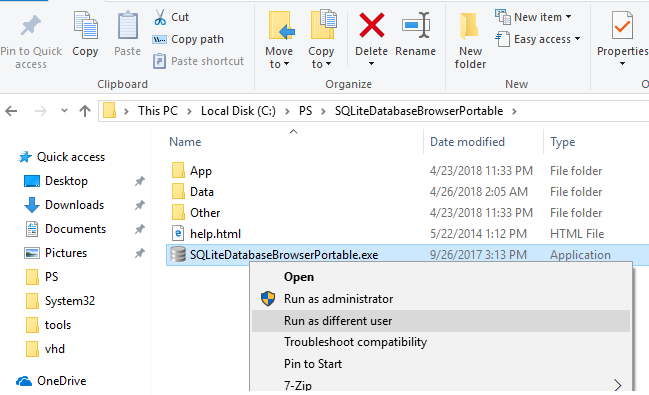
The easiest way to run an application on behalf of another user is to use the Windows File Explorer GUI. Just find an application (or a shortcut) you want to start, press the Shift key and right-click on it. Select Run as different user in the context menu.
[alert]Note. If the menu item “Run as different user” is missing, see the next section.
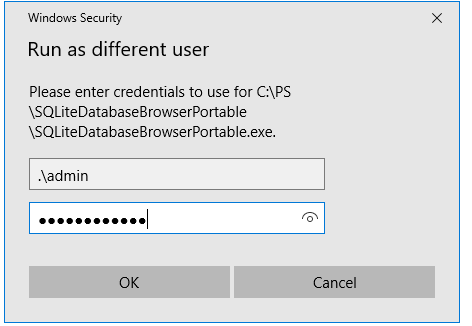
In the next window, specify the name and password of the user under whose account you want to run the application and click OK.
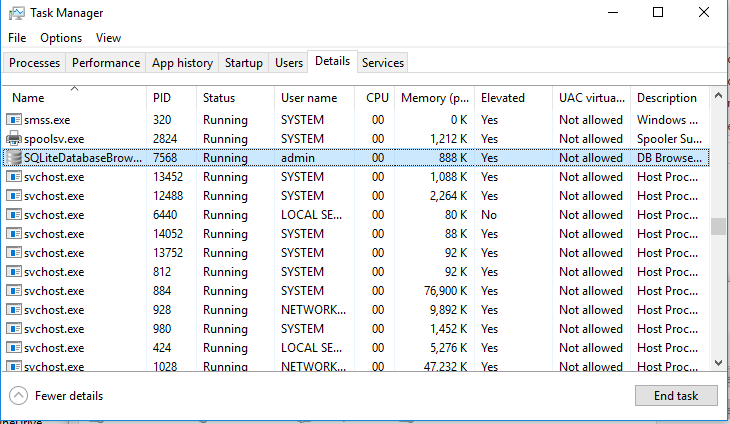
Open the Task Manager and make sure that the application is running under the specified user account.
“Run As Different User” Option is Missing in Windows 10
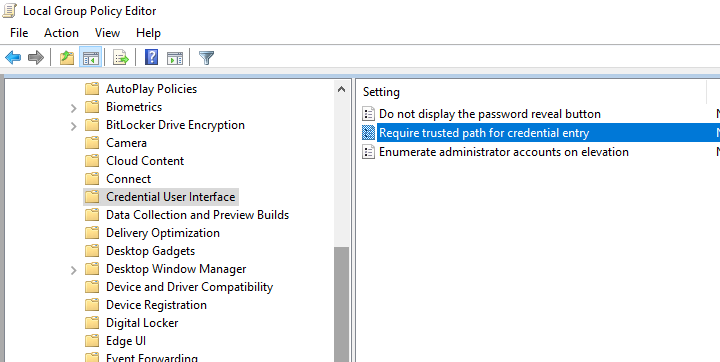
If there is no Run as different user option in the File Explorer context menu, open the Local Group Policy Editor ( gpedit.msc ) and make sure that the Require trusted path for credential entry policy is disabled (or not configured) in Computer Configuration -> Administrative Templates -> Windows Components -> Credential User Interface.
Using the RunAs Command to Run a Program as Another User from CMD
You can use the Windows built-in cli tool runas.exe to run apps applications as a different user from the command prompt. The runas command also lets you to save the user’s password to the Windows Credential Manager so that you don’t have to enter it every time.
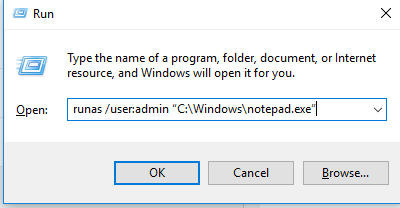
Open the command prompt (or the Run window by pressing Win+R). To start the Notepad.exe under the administrator account, run this command:
runas /user:admin «C:\Windows\notepad.exe»
runas /user:»antony jr» notepad.exe
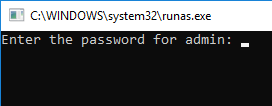
In the next window, the prompt “Enter the password for admin” appears, where you have to enter the user’s password and press Enter.
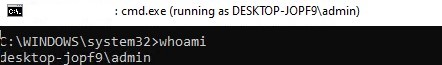
Your application should open. In my case, this is cmd.exe. The window title says “running as PCName\username“:
For example, you can open the Control Panel under a different user:
runas /user:admin control
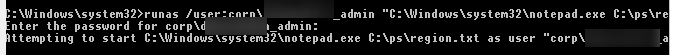
If you need to run a program under a domain user, use the following name format: UserName@DomainName or DomainName\UserName . For example, to open a text file using notepad on behalf of a domain user, use the command:
runas /user:corp\server_admin «C:\Windows\system32\notepad.exe C:\ps\region.txt»
Sometimes you need to run a program as a domain user from a computer that is not joined to the AD domain. In this case, you need to use the following command (It is assumed that the DNS server specified in your computer’s network settings can resolve this domain name):
runas /netonly /user:contoso\bmorgan cmd.exe
If you don’t want to load user profile when starting the program as different user, use the /noprofile parameter. This allows the application to launch much faster, but may cause incorrect operation of programs that store app data in the user’s profile.
How to Use RunAs Without Password Prompt?
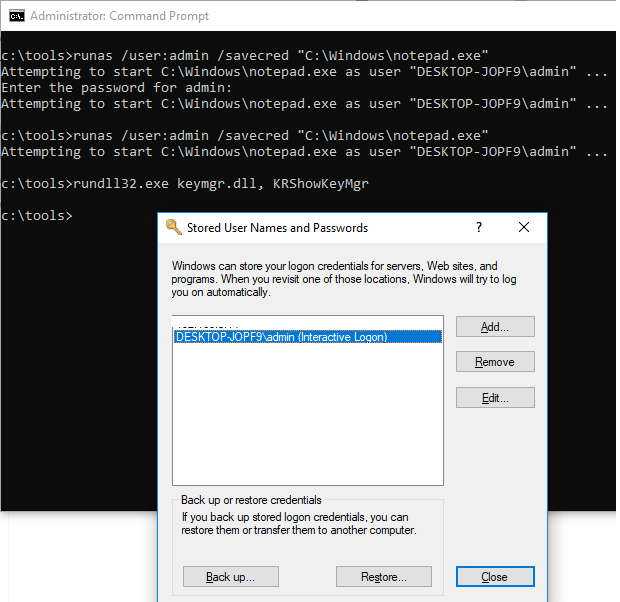
You can save the user credentials (with password) that you enter. The /savecred parameter is used for this.
runas /user:admin /savecred “C:\Windows\cmd.exe”
After specifying the password, it will be saved to the Windows Credential Manager.
The next time you run the runas command under the same user with the /savecred key, Windows will automatically use the saved password from the Credential Manager without prompting to enter it again.
To display a list of saved credentials in Credential Manager, use the following command:
rundll32.exe keymgr.dll, KRShowKeyMgr
However, using the /savecred parameter is not safe. Because a user, in which profile it is saved, can use it to run any command with these privileges and even change another user password. Also, it is easy to steal passwords saved in the Credential Manager so it is recommended to prevent a Windows from saving passwords (and never save the password of the privileged administrator accounts).
How to Create a Shortcut to Run As Different User?
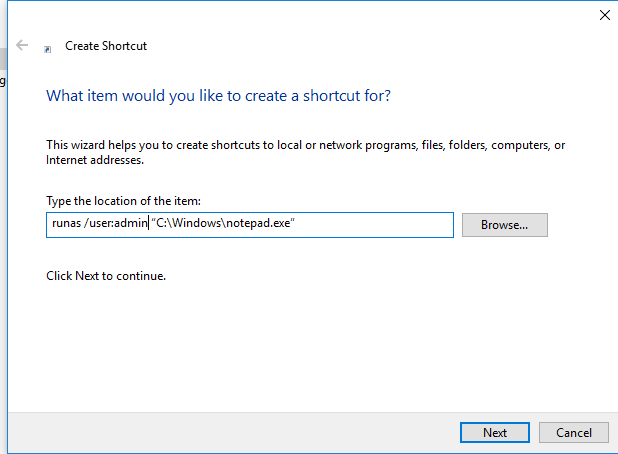
You can create a shortcut on your desktop that allows you to run the program as a different user. Just create a new shortcut, and specify the runas command with the necessary parameters in the Location field
When you run such a shortcut, you will be prompted to enter a user password.
If you additionally specify the /savecred parameter in the runas shortcut, then the password will be prompted only once. The password will be saved in Credential Manager and automatically used when you running the shortcut without prompting for a password.
Such shortcuts are quite often used to run programs that require elevated permissions to run. However, there are safer ways to run a program without administrator privileges, or disable the UAC prompt for a specific application.
How to Run MMC Snap-Ins As a Different User?
In some cases, you have to run one of Windows management snap-ins as a different user. For example, you can use the following command to run the Active Directory Users and Computers (ADUC) RSAT snap-in as a different user:
runas.exe /user:DOMAIN\USER «cmd /c start \»\» mmc %SystemRoot%\system32\dsa.msc»
In the same way you can run any other snap-in (if you know its name).
Add “Run As” Option to Start Menu in Windows 10
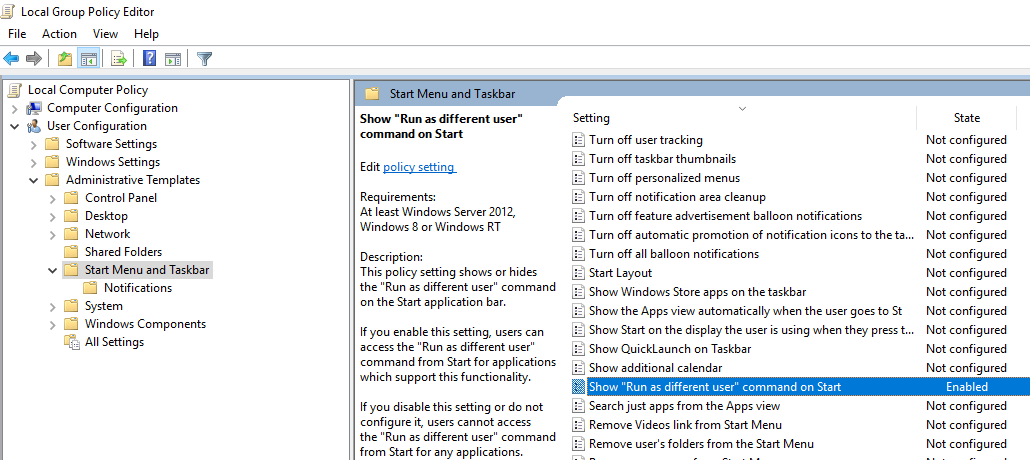
By default in Windows 10 Start Menu items do not have the “Run As” option. To add the context menu “Run as different user”, enable the “Show Run as different user command on Start” policy in User Configuration -> Administrative Templates ->Start Menu and Taskbar section of the Local Group Policy Editor (gpedit.msc).
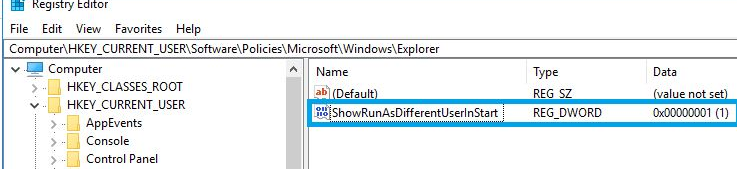
Or, if the gpedit.msc is missing, create a new DWORD parameter with the name ShowRunasDifferentuserinStart and value 1 in the registry key HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Explorer. You can use the following PowerShell command to add the reg parameter:
New-ItemProperty -Path «HKCU:\Software\Policies\Microsoft\Windows\CurrentVersion\Explorer» -Name ShowRunasDifferentuserinStart -Value 1 -PropertyType DWORD -Force
Update the Group Policy settings ( gpupdate /force ) and make sure that a new context menu More -> Run as different user has appeared for the programs in the Start menu.
Service User Accounts
Each service executes in the security context of a user account. The user name and password of an account are specified by the CreateService function at the time the service is installed. The user name and password can be changed by using the ChangeServiceConfig function. You can use the QueryServiceConfig function to get the user name (but not the password) associated with a service object. The service control manager (SCM) automatically loads the user profile.
When starting a service, the SCM logs on to the account associated with the service. If the log on is successful, the system produces an access token and attaches it to the new service process. This token identifies the service process in all subsequent interactions with securable objects (objects that have a security descriptor associated with them). For example, if the service tries to open a handle to a pipe, the system compares the service’s access token to the pipe’s security descriptor before granting access.
The SCM does not maintain the passwords of service user accounts. If a password is expired, the logon fails and the service fails to start. The system administrator who assigns accounts to services can create accounts with passwords that never expire. The administrator can also manage accounts with passwords that expire by using a service configuration program to periodically change the passwords.
If a service needs to recognize another service before sharing its information, the second service can either use the same account as the first service, or it can run in an account belonging to an alias that is recognized by the first service. Services that need to run in a distributed manner across the network should run in domain-wide accounts.
You can specify one of the following special accounts instead of specifying a user account for the service:
Run a process from a windows service as the current user
I currently have a windows service that is running under the System Account. My problem is that i need to start certain processes from within the service as the current logged on user. I have all the code etc to get the current logged on user / Active session.
My problem is that i need spawn a process as the logged on user but will not know the user credentials etc.
The service is .net compiled service and i expect that i need to use some Pinvoke methods to get a handle of one of the current users process in order to duplicate it and lunch as process with the handle.
Unfortunately i cannot find any good documentation / solution on how to implement it?
If someone is able to give me some guidance / example i would highly appreciate it.
* Updated * I think i have explained this incorrectly and need to reajust according to what i actually require. I do not necessarily want to launch a new process, i just want to impersonate the logged on user. I have been so wrapped up at looking at CreateProcess etc i have lead myself down a path of create a new process as the current logged in user (which is not particularly what i want to do).
In turn i just want to run some code under the current user context (Impersonate the current Logged on user)?
2 Answers 2
One option is to have background application that automatically starts when user logs on and listens to commands from your service through WCF, or thrift, or by just monitoring some file and reading command from there.
Another option is to do what you originally asked for — launch using windows API. But the code is quite scary. Here is a sample, that you can use. It will execute any command line under currently active user session, with CreateProcessInConsoleSession method:
As is so common with these types of questions about Windows services, you’re operating in the mindset of a single-user operating system. The whole reason you decided to write your app as a service was because you were running into conflicts between your mental model of a single-user OS and the reality of a multi-user OS. Unfortunately, a service didn’t solve all of your problems and now you’re trying to figure out how to accomplish step two in the ultimately-doomed hacked design.
The fact is, you cannot be guaranteed that there is a «logged on user». If no one has logged on to the workstation, there will be no one logged on, yet your service will still be running.
Even if you somehow got past this by ensuring that someone will always be logged on (impossible), then you would run into the situation where multiple users are logged on. Then which one should your service start the process as? Should it just pick one of them randomly?
And is it necessary in your case to distinguish between users logged on locally to the console and those who are logged on remotely? Remember that remote users won’t have a local console.
If you could somehow get past all of these hurdles (unfortunately, probably by burying your head in the sand and continuing to pretend that Windows is a single-user OS), you could make use of the WTSGetActiveConsoleSessionId function to obtain the current session ID, the WTSQueryUserToken function to obtain the user token corresponding to that session ID, and then finally the CreateProcessAsUser function to launch your process in the context of that user. If there is one. And they have the appropriate privileges. And the physical console is not attached to a dummy session. And you’re not running a server SKU that allows multiple active console sessions. And…
If you could decide on a particular user whose account you wish to use to start the auxiliary process, you could log on that user, manipulate their user token, execute the process, and finally close the process and log out the user. The CreateProcessWithLogonUser function wraps up a lot of this drudgery for you, making the code a lot more svelte. But appearances can be deceiving, and this still has some massive security implications that you probably do not completely understand if you’re asking this question in the first place. And you really cannot afford to not understand security risks like this.
Besides, users that are logged in with LogonUser (which is done for you automatically when you use the CreateProcessWithLogonUser function) lack a window station and desktop on which they can launch interactive processes. So if the process you wish to launch in the context of that user will show any kind of UI, you’re out of luck. Windows will kill your app as soon as it tries to access a desktop for which it lacks the requisite permissions. There is no way, from a Windows service, to obtain the handle of a desktop that will be useful to you (which goes a long way towards explaining the general rule you probably already know, that services cannot display any type of UI).