- Working well with enhanced Point and Print
- Windows 8 Client Connection Behavior
- Windows 7 and Windows Vista Client Connection Behavior
- Установка принтеров пользователям домена AD с помощью групповых политик
- Подключение принтеров пользователям через GPO
- Настройка политики подключения принтеров Point and Print Restrictions
- The Blog
- Windows 10 Point Print UAC Prompt Cause
- How to fix Windows 10 point print UAC
- Part 1
- Part 2
- Windows point and printing
- Answered by:
- Question
- Answers
- All replies
Working well with enhanced Point and Print
The updated printer sharing mechanism is referred to as enhanced Point and Print, and it allows print clients to print to v4 shares without downloading the manufacturer-provided device driver from the print server.
Because client machines do not download the entire driver package when they connect with a print server that has enhanced Point and Print and v4 printer drivers, it is important to be aware of the following architectures. This information should help you to develop and package your v4 printer driver appropriately.
Windows 8 Client Connection Behavior
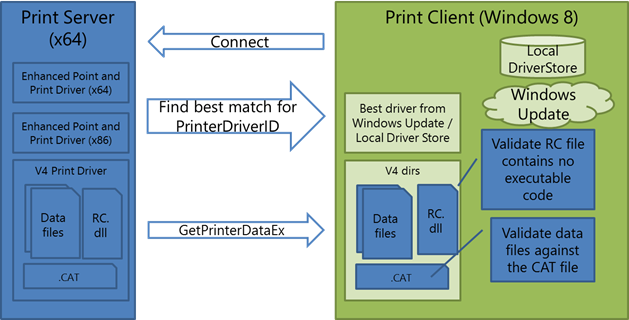
When a Windows 8 client connects to a shared print queue that is using a v4 printer driver, the client will try to obtain a driver that supports client side rendering. The client searches the local DriverStore for a driver with a HardwareID that matches the server driver’s PrinterDriverID. If one is found, that driver will be installed locally. Otherwise, the client will connect using the enhanced Point and Print driver.
In both cases, the client downloads configuration data from the server using GetPrinterDataEx calls. The configuration data includes data files like generic printer description (GPD) files, PostScript printer description (PPD) files, the driver property bag, JavaScript constraints and a resource DLL. The client also downloads the CAT file that was associated with the server’s driver.
The print system then examines the client and validates that the resource DLL contains no executable code. The print system also verifies that the downloaded files are valid and signed by the CAT file downloaded from the server. Any files that are untrusted will be deleted. The following diagram illustrates this configuration-related communication between a WindowsВ 8 client and shared print servers that use the v4 printer driver.
Windows 7 and Windows Vista Client Connection Behavior
WindowsВ 7 and WindowsВ Vista clients may also connect to shared print queues that use a v4 printer driver. In this case, however, the client will always download the enhanced Point and Print driver from the server. This driver uses server side rendering to ensure that the proper printer description language (PDL) is generated for the printer.
Configuration data is downloaded from the server in the same way for Windows 7 and Windows Vista client connections, using GetPrinterDataEx calls. If any downloaded files fail validation against the server’s CAT file, they are deleted. The following diagram illustrates this configuration-related communication between a Windows 7 or a Windows Vista client and shared print servers that use the v4 printer driver.
Shared printers that are backed by a v3 printer driver will continue to work using the existing Point and Print system.
Установка принтеров пользователям домена AD с помощью групповых политик
Рассмотрим возможности автоматического подключения принтеров пользователям домена Active Directory с помощью групповых политик (GPO). Довольно удобно, когда при первом входе в систему у пользователя сразу устанавливаются и появляются в принтерах доступные ему устройства.
Рассмотрим следующую конфигурацию: в организации имеется 3 отдела, каждый отдел должен печатать документы на собственном цветном сетевом принтере. Ваша задача, как администратора, настроить автоматическое подключение сетевых принтеров пользователям в зависимости от отдела.
Подключение принтеров пользователям через GPO
Создайте три новые группы безопасности в AD (prn_HPColorSales, prn_HPColorIT, prn_HPColorManagers) и добавьте в нее пользователей отделов (наполнение групп пользователей можно автоматизировать по статье “Динамические группы в AD”). Вы можете создать группы в консоли ADUC, или с помощью командлета New-ADGroup:
New-ADGroup «prnHPColorSales» -path ‘OU=Groups,OU=Moscow,DC=corp,dc=winitpro,DC=ru’ -GroupScope Global –PassThru
- Запустите консоль редактора доменных политик (GPMC.msc), создайте новую политику prnt_AutoConnect и прилинкуйте ее к OU с пользователями;
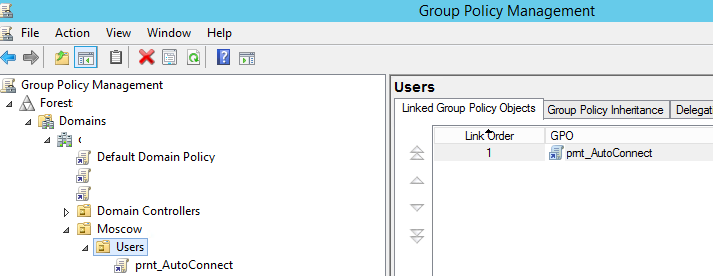
При использовании такой групповой политики, новые принтера будут устанавливаться у пользователей, только если на их компьютере уже установлен соответствующий принтеру драйвер печати. Дело в том, что у обычных пользователей нет прав на установку драйверов.
Настройка политики подключения принтеров Point and Print Restrictions
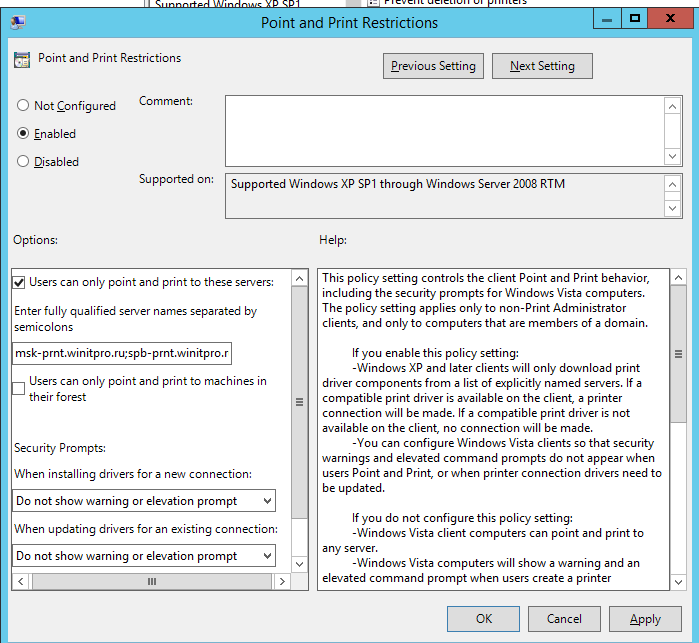
Для корректного подключения принтеров у любого пользователя, вам придется настроить политику Point and Print Restrictions и настроить адреса принт-серверов серверов, с которых пользователей разрешено устанавливать принтеры.
Если вы подключаете принтеры через пользовательский раздел политики, перейдите в раздел GPO User Configuration -> Policy -> Administrative Templates -> Control Panel -> Printers -> Printer -> Point and Print Restriction. Включите политику (Enabled) и настройте ее следующим образом:
- Users can only point and print to these servers –укажите список принт-серверов, с которых разрешено устанавливать драйвера (указываются FQDN имена, разделитель точка с запятой);
- When installing driver for new connection -> Do not show warning or elevation prompt
- When installing driver for existing connection -> Do not show warning or elevation prompt.
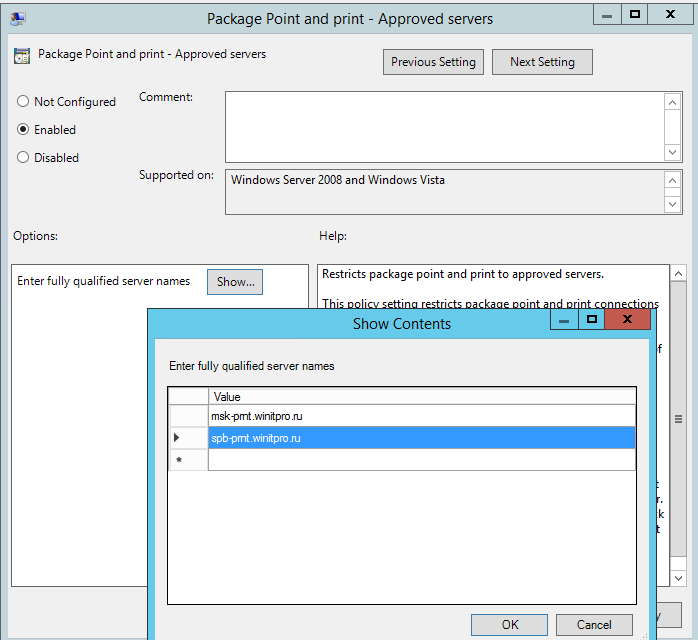
Аналогичным образом нужно включить политику Package Point and Print – Approved server в разделе User Configuration -> Policies -> Administrative Templates -> Printers и задать в ней список доверенных принт-серверов.
Теперь после перезагрузки компьютера при входе пользователя у него будет автоматически подключаться назначенный ему сетевой принтер.
The Blog
Jonathan Lefebvre November 3, 2016 WINDOWS 10 13 Comments
We came across a strange issue today on Windows 10 devices that we haven’t seen since the Windows Vista days. Users have started to get prompts for User Account Control(UAC) when connecting to some printers. The Point and Print feature is responsible for this as it easily allows standard users to install printer drivers from the trusted print server. This post describes how to fix Windows 10 point print UAC problem.
The problem appeared right after applying last July monthly updates. (MS16-087)
[su_box title=”Description” style=”glass” title_color=”#F0F0F0″]This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if an attacker is able to execute a man-in-the-middle (MiTM) attack on a workstation or print server, or set up a rogue print server on a target network.[/su_box]
Windows 10 Point Print UAC Prompt Cause
Microsoft as tightened the requirement for printer drivers on print servers.
- Are using a print server
- Allow standard user to install printer drivers using the Point and Print Group Policy
- Are using old printer driver that might have the following :
- Non-package-aware v3 printer drivers
- Unsigned or expired certificate validation drivers
Following MS16-087 installation, you receive a UAC prompt and a Connect to Printer error after a printer installation attempt. (A policy is in effect on your computer which prevents you from connecting to this print queue. Please contact your system Administrator)

Here’s the list of the specific KB per OS that create the issue :
- KB3163912
- Windows 10
- KB3172985
- Windows 10 v1511
- KB3170455
- Windows Vista
- Windows 7
- Windows 8.1
- Windows Server 2008
- Windows Server 2008 R2
- Windows Server 2012
- Windows Server 2012 R2
How to fix Windows 10 point print UAC
Part 1
Part 1 of the solution is available in the October 2016 Preview of Monthly Quality Rollup available for all operating system except Windows 10 (October 16th). Microsoft has released an update that lets network administrators configure policies that permit the installation of print drivers that they consider are safe. This update also allows network administrators to deploy printer connections that they consider safe.
[su_box title=”Note” style=”glass” title_color=”#F0F0F0″]If you are not familiar with preview updates, take a look at the following blog post.[/su_box]
This mean, if you are facing the issue, the official fix for it will be available for production use on the next Patch Tuesday (November 8th) as part of the Monthly Quality Rollup.
[su_box title=”Important” style=”glass” box_color=”#000000″ title_color=”#F0F0F0″]**Update 2016/11/10** Microsoft as released an update that was in preview in Octobre 2016. KB3197868 https://support.microsoft.com/en-ca/kb/3197868 After testing, it’s working as excepted. The second GPO part still required to make this work.[/su_box]
KB in preview
KB in production
Part 2
Part 2 consist having the right GPO settings for Point and Print.
Two GPO settings must be applied :
- Under Computer Configuration / Policies / Administrative Templates / Printers, set Package Point and Print – Approved server to Enabled
- Each print server must be added to the list with the fully qualified server name
- Under Computer Configuration / Policies / Administrative Templates / Printers, set Point and Print Restrictions to Enabled
- Each print server must be added to the list with the fully qualified server name, seperated by semi-colons
- When installing driver for new connection, select Do not show warning or elevation prompt
- When installing driver for existing connection, select Do not show warning or elevation prompt
How useful was this post?
Click on a star to rate it!
Average rating 5 / 5. Vote count: 3
No votes so far! Be the first to rate this post.
Contributor of System Center Dudes. Based in Montreal, Canada, Senior Microsoft SCCM consultant, working in the industry for more than 10 years. He developed a strong knowledge of SCCM and MDT to build automated OS deployment solution for clients, managed large and complexe environment, including Point of Sale (POS) related projects.
Windows point and printing
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Answered by:
Question
It seems Point and Print group policy is not applying to Windows 10 1607. I am getting UAC prompts when I try to add a shared printer. The policy is working correctly under all other versions of Windows including Windows 10 1511. Is there any workaround for this?
Answers
The KB3163912 is definitely the problem.
Which will prevent to install drivers which are not «PackageAware».
You can check on your PrintServer which Printers have not PackageAware Drivers:
Get-PrinterDriver | Where-Object < $_ . IsPackageAware>| select name
The only thing that you can do is to pre-deploy your PrinterDrivers to the WindowsDriver Store. or uninstall the CU which is not really a solution.
- Marked as answer by MeipoXu Microsoft contingent staff Monday, September 12, 2016 7:28 AM
All replies
Maybe related: https://social.technet.microsoft.com/Forums/en-US/030ee94a-047d-460a-bc39-52351a199364/kb3163912-breaks-point-and-print-restrictions-gpo-settings?forum=winserverGP
Please remember to mark the replies as answers if they help, and unmark the answers if they provide no help.
Hi Jeff Poblocki ,
We could check the link Sven J provided. We could try remove the KB3169912 to check. It could be caused GP issue.
Considering the Anniversary Update is released recently, if the issue persists, you could try the built-in «Feedback» tool to submit the issue on your side.
Hope it will be helpful to you
Please remember to mark the replies as an answers if they help and unmark them if they provide no help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com.
We could check the link Sven J provided. We could try remove the KB3169912 to check. It could be caused GP issue.
Considering the Anniversary Update is released recently, if the issue persists, you could try the built-in «Feedback» tool to submit the issue on your side.
Hope it will be helpful to you
Please remember to mark the replies as an answers if they help and unmark them if they provide no help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com.
Please remember to mark the replies as answers if they help, and unmark the answers if they provide no help.
The KB3163912 is definitely the problem.
Which will prevent to install drivers which are not «PackageAware».
You can check on your PrintServer which Printers have not PackageAware Drivers:
Get-PrinterDriver | Where-Object < $_ . IsPackageAware>| select name
The only thing that you can do is to pre-deploy your PrinterDrivers to the WindowsDriver Store. or uninstall the CU which is not really a solution.
- Marked as answer by MeipoXu Microsoft contingent staff Monday, September 12, 2016 7:28 AM
you are right, i did my testing again.
You can take a look at c:\windows\inf\setupapi.dev.log file for the file or reason behind the prompts. Rename the file to .old, then add the connection. When you get the prompt, click Cancel and open the log. Search for . there will be some indication what is happening during the connection. The driver files will be downloaded to a temp location on the machine, but the failure will typically be when placing the files in the DriverStore directory.
It looks like configuring the Point and Print Restrictions policy will no longer get past the download prompt for the client.
Alan Morris formerly with Windows Printing Team
Thanks for using the print commandlets for PowerShell.
Alan Morris formerly with Windows Printing Team