- Управление паролями в Linux с помощью команды passwd
- Команда passwd
- Синтаксис PASSWD
- Смена пароля обычного пользователя
- Вывод информации о статусе пароля
- Удаление пользовательского пароля
- Блокировка пароля пользователя
- Дезактивация пароля
- How To Linux Set or Change User Password
- Linux Set User Password
- Linux change password for other user account
- Linux Change Group Password
- Changing user passwords on Linux
- Forcing Linux user to change password at their next login
- Locking and Unlocking user password of the named account
- A note about setting up a secure Linux password
- Conclusion
- How To Set Password Policies In Linux
- Set Password Policies In Linux
- Set password length in DEB based systems
- Set password length in RPM based systems
- Set password complexity in DEB based systems
- Set password complexity in RPM based systems
- Set password expiration period in DEB based systems
- Set password expiration period in RPM based systems
- Forbid previously used passwords in DEB based systems
- Forbid previously used passwords in RPM based systems
Управление паролями в Linux с помощью команды passwd
Оригинал: Password Management in Linux by using passwd command
Автор: Naga Ramesh
Дата публикации: 30 апреля 2016 года
Перевод: А. Кривошей
Дата перевода: апрель 2017 г.
Пароль в Linux — это последовательность символов без пробелов, используемая для идентификации пользователя в операционной системе. Обычно в многопользовательской или хорошо защищенной однопользовательской системе каждому пользователю присваивается уникальное имя (называемое user ID), которое не является секретом. Если пользователь вводит опеределенный ID, необходимо убедиться, что это действительно он. Для этого служит пароль, который знает только этот пользователь. Большинство сетей требуют от своих пользователей периодической смены паролей.
Команда passwd
Команда passwd используется для создания и изменения пользовательских паролей. Обычный пользователь может запустить passwd, чтобы сменить свой собственный пароль, а системный администратор (суперпользователь root) может изменять пароли других пользователей, либо опеределять правила использования и смены пользовательских паролей.
Синтаксис PASSWD
Смена пароля обычного пользователя
Если вы авторизованы как обычный пользователь (в моем случае user1), запуск команды passwd сбрасывает пароль пользователя.
Если вы авторизованы как root, то при запуске команды passwd по умолчанию сбрасывается пароль root, а если вы зададите после команды имя пользователя, то можете сменить пароль этого пользователя.
Вывод информации о статусе пароля
Для показа информации о статусе пароля пользователя используется опция -S команды passwd.
В приведенном выше выводе команды первое поле показывает имя пользователя, затем статус пароля ( PS = Password Set (пароль задан) , LK = Password locked (пароль заблокирован) , NP = No Password (нет пароля) ). Третье поле отображает время последнего изменения пароля, а четвертое и последнее поле — минимальный и максимальный срок действия пароля, срок вывода предупреждения и срок дезактивации пароля.
Мы также можем вывести информацию о статусе паролей всех пользователей с помощью опции –Sa.
Удаление пользовательского пароля
Мы можем удалить пароль заданного пользователя с помощью опции -d.
Блокировка пароля пользователя
С помощью опции «-l» команды passwd можно заблокировать пароль пользователя. Пока пароль заблокирован, пользователь не сможет сменить его.
Для разблокировки пользовательского пароля используется опция -u.
Дезактивация пароля
С помощью опции -i вы можете дезактивировать пароль пользователя, если через «n» дней после истечения срока действия пароля он не сменил его. После этого пользователь не сможет авторизоваться в системе.
С помощью опции -n мы можем задать минимальное количество дней, через которое пользователь сможет сменить пароль. Нулевое значение позволяет менять пароль в любое время.
С помощью опции -w можно задать, за сколько дней до истечения срока действия пароля пользовать получит предупреждение об этом.
Источник
How To Linux Set or Change User Password
Linux Set User Password
Type following passwd command to change your own password:
$ passwd
Sample Outputs:
The user is first prompted for his/her old password if one is present. This password is then encrypted and compared against the stored password. The user has only one chance to enter the correct password. The super user is permitted to bypass this step so that forgotten passwords may be changed. A new password is tested for complexity. As a general guideline, passwords should consist of 10 to 20 characters including one or more from each of following sets:
- Lower case alphabetics
- Upper case alphabetics
- Digits 0 thru 9
- Punctuation marks/spacial characters
Linux change password for other user account
You need to login as the root user, type the following command to change password for user vivek:
# passwd vivek
OR
$ sudo passwd vivek
Sample putput:
- vivek – is username or account name.
Passwords do not display to the screen when you enter them. For example:
Linux changing user password using passwd
Linux Change Group Password
When the -g option is used, the password for the named group is changed. In this example, change password for group sales:
# passwd -g sales
The current group password is not prompted for. The -r option is used with the -g option to remove the current password from the named group. This allows group access to all members. The -R option is used with the -g option to restrict the named group for all users.
Changing user passwords on Linux
As a Linux system administrator (sysadmin) you can change password for any users on your server. To change a password on behalf of a user:
- First sign on or “su” or “sudo” to the “root” account on Linux, run: sudo -i
- Then type, passwd tom to change a password for tom user
- The system will prompt you to enter a password twice
To change or set a new root (superuser) password type:
$ sudo passwd
Forcing Linux user to change password at their next login
By default, Linux passwords never expire for users. However, we can force users to change their password the next time they log in via GUI or CLI methods. The syntax is straightforward:
$ sudo passwd -e
$ sudo passwd —expire
Let us immediately expire an account’s password:
$ sudo passwd -e marlena
The system will confirm it:
When user try to login via ssh command, they will see the following on screen:
Locking and Unlocking user password of the named account
Note that the following local command does not disable the account. The user may still be able to login using another authentication token, such as an SSH key. To disable the account, administrators should use either usermod —expiredate 1
We can lock the password as follows:
$ sudo passwd -l
This option disables a password by changing it to a value which matches no possible encrypted value (it adds a ! at the beginning of the password in the /etc/shadow file. Want to unlock the password, try:
$ sudo passwd -u
The above command option re-enables a password by changing the password back to its previous value. In other words, to the value before using the -l option.
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
A note about setting up a secure Linux password
Compromises in password security typically result from careless password selection. Avoid common password such as:
- Words which appears in a dictionary
- Your first and last name
- Pet names
- Kids or spouses names
- License number
- Date of birth (DoB)
- Home or office address
I strongly recommend that you generate a unique password for all user accounts using your chosen password manager.
Conclusion
The passwd command line utility is used to update or change user’s password. The encrypted password is stored in /etc/shadow file and account information is in /etc/passwd file. To see all user account try grep command or cat command as follows:
$ cat /etc/passwd
$ grep ‘^userNameHere’ /etc/passwd
$ grep ‘^tom’ /etc/passwd
The guidance given in this quick tutorial should work with any Linux distribution, including Alpine, Arch, Ubuntu, Debian, RHEL, Fedora, Oracle CentOS, SUSE/OpenSUSE and other popular Linux distros.
🐧 Get the latest tutorials on Linux, Open Source & DevOps via
Источник
How To Set Password Policies In Linux
Even though Linux is secure by design, there are many chances for the security breach. One of them is weak passwords. As a System administrator, you must provide a strong password for the users. Because, mostly system breaches are happening due to weak passwords. This tutorial describes how to set password policies such as password length, password complexity, password expiration period etc., in DEB based systems like Debian, Ubuntu, Linux Mint, and RPM based systems like RHEL and CentOS.
Set Password Policies In Linux
By default, all Linux operating systems requires password length of minimum 6 characters for the users. I strongly advice you not to go below this limit. Also, don’t use your real name, parents/spouse/kids name, or your date of birth as a password. Even a novice hacker can easily break such kind of passwords in minutes. The good password must always contains more than 6 characters including a number, a capital letter, and a special character.
Set password length in DEB based systems
Usually, the password and authentication-related configuration files will be stored in /etc/pam.d/ location in DEB based operating systems.
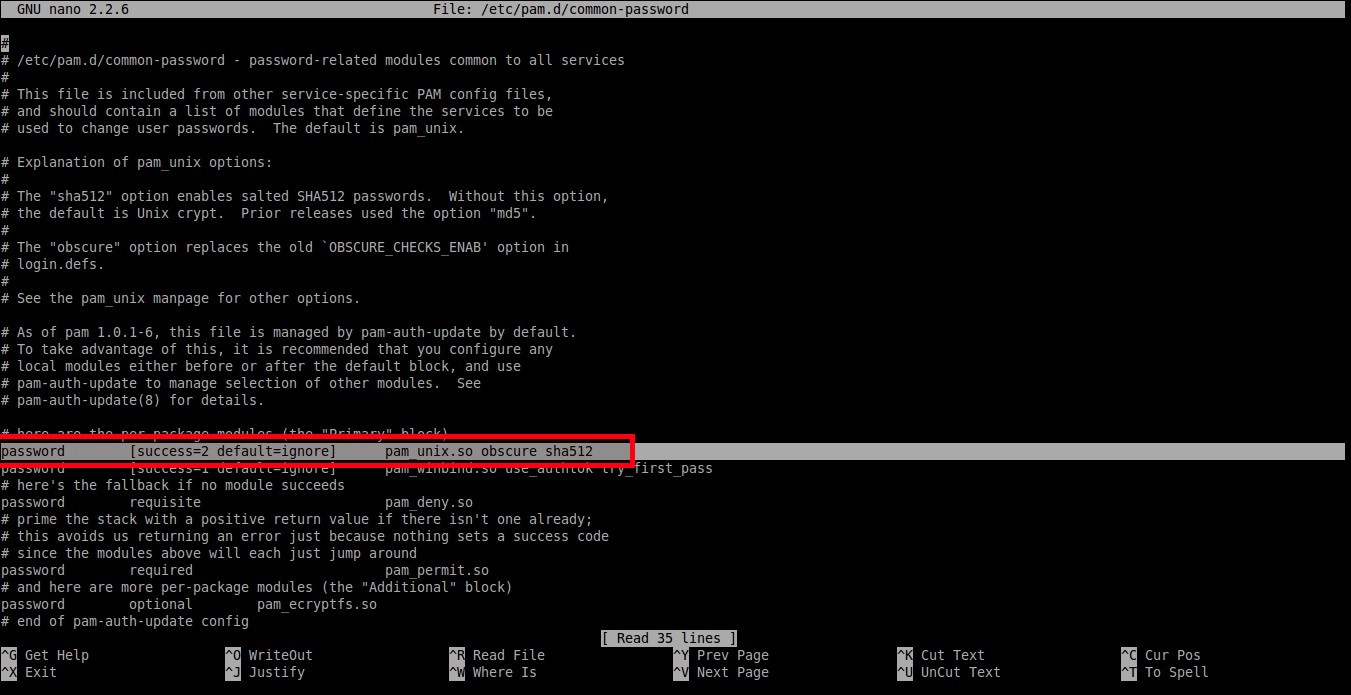
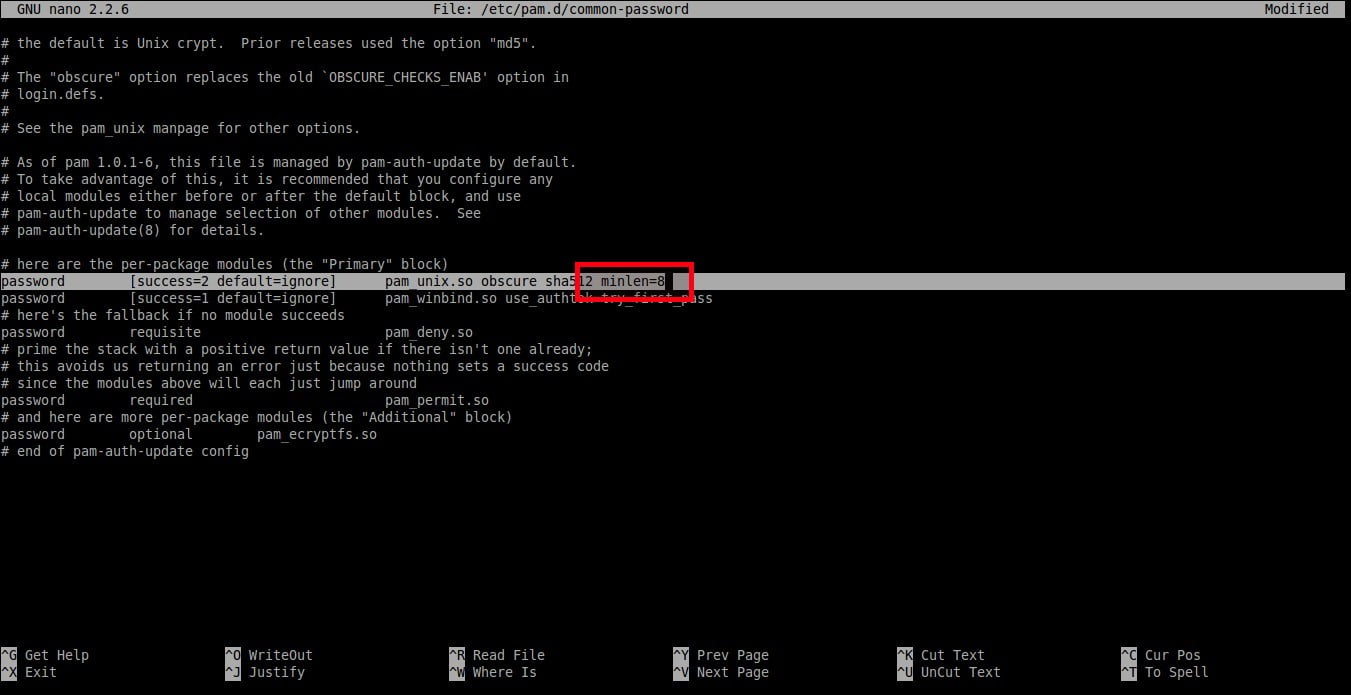
To set minimum password length, edit/etc/pam.d/common-password file;
Find the following line:
And add an extra word: minlen=8 at the end. Here I set the minimum password length as 8.
Set password length on DEB-based systems
Save and close the file. Now the users can’t use less than 8 characters for their password.
Set password length in RPM based systems
In RHEL, CentOS 7.x systems, run the following command as root user to set password length.
To view the minimum password length, run:
Sample output:
In RHEL, CentOS 6.x systems, edit /etc/pam.d/system-auth file:
Find the following line and add the following at the end of the line:
Set password length on RPM-based systems.
As per the above setting, the minimum password length is 8 characters.
Set password complexity in DEB based systems
This setting enforces how many classes, i.e upper-case, lower-case, and other characters, should be in a password.
First install password quality checking library using command:
Then, edit /etc/pam.d/common-password file:
To set at least one upper-case letters in the password, add a word ‘ucredit=-1’ at the end of the following line.
Set password complexity in DEB based systems
Set at least one lower-case letters in the password as shown below.
Set at least other letters in the password as shown below.
As you see in the above examples, we have set at least (minimum) one upper-case, lower-case, and a special character in the password. You can set any number of maximum allowed upper-case, lower-case, and other letters in your password.
You can also set the minimum/maximum number of allowed classes in the password.
The following example shows the minimum number of required classes of characters for the new password:
Set password complexity in RPM based systems
In RHEL 7.x / CentOS 7.x :
To set at least one lower-case letter in the password, run:
To view the settings, run:
Sample output:
Similarly, set at least one upper-case letter in the password using command:
To view the settings:
Sample output:
To set at least one digit in the password, run:
To view the setting, run:
Sample output:
To set at least one other character in the password, run:
To view the setting, run:
Sample output:
In RHEL 6.x / CentOS 6.x systems, edit /etc/pam.d/system-auth file as root user:
Find the following line and add the following at the end of the line:
As per the above setting, the password must have at least 8 characters. In addition, the password should also have at least one upper-case letter, one lower-case letter, one digit, and one other characters.
Set password expiration period in DEB based systems
We are going to set the following policies.
- Maximum number of days a password may be used.
- Minimum number of days allowed between password changes.
- Number of days warning given before a password expires.
To set this policy, edit:
Set the values as per your requirement.
Set password expiration period in DEB based systems
As you see in the above example, the user should change the password once in every 100 days and the warning message will appear 7 days before password expiration.
Be mindful that these settings will impact the newly created users.
To set maximum number of days between password change to existing users, you must run the following command:
To set minimum number of days between password change, run:
To set warning before password expires, run:
To display the password for the existing users, run:
Here, sk is my username.
Sample output:
As you see in the above output, the password never expires.
To change the password expiration period of an existing user,
The above command will set password of the user ‘sk’ to expire on 24/06/2018. Also the the minimum number days between password change is set 5 days and the maximum number of days between password changes is set to 90 days. The user account will be locked automatically after 10 days and It will display a warning message for 10 days before password expiration.
Set password expiration period in RPM based systems
This is same as DEB based systems.
Forbid previously used passwords in DEB based systems
You can limit the users to set a password which is already used in the past. To put this in layman terms, the users can’t use the same password again.
To do so, edit/etc/pam.d/common-password file:
Find the following line and add the word ‘remember=5’ at the end:
The above policy will prevent the users to use the last 5 used passwords.
Forbid previously used passwords in RPM based systems
This is same for both RHEL 6.x and RHEL 7.x and it’s clone systems like CentOS, Scientific Linux.
Edit /etc/pam.d/system-auth file as root user,
Find the following line, and add remember=5 at the end.
Suggested read:
You know now what is password policies in Linux, and how to set different password policies in DEB and RPM based systems.
Источник