How do I find my network information — in Linux?
Taking a cue from Martin’s helpful article (see «How do I find my IP Address») I thought it would be a good idea to offer the same information for the Linux operating system. But with Linux there is one issue to get around — that of the number of different tools available to use to find this information. Because there are so many graphical tools with which to find networking information, I thought it would be best to simply tackle this with everyone’s favorite tool — the command line.
In this article I will show you how to find out various networking information on your Linux system. All of these tasks can be handled by any skill level of user, so don’t think you have to be an ubergeek, hacker-type in order to gain this information.
IP Address

Let’s start off with the IP Address. Of course, before you do anything, you need to open up a terminal window. Once you have that open you can then issue the necessary command. The command for finding your IP Address is ifconfig. When you issue this command you will receive information for every network connection you have available. Most likely you will see information for both the loopback (lo) and your wired network connection (eth0). If you have a wireless connection that will be listed, most likely, as wlan0. The reported information will look like that shown in Figure 1. As you can see, you not only get the IP Address, but the Broadcast address, the Subnet Mask, and the IPv6 Address.
Hostname
From that same command line, if you enter the command hostname you will see the actual hostname of your machine. In the case of my test machine, I see Ubuntu-desktop. Â For more information on using this command, take a look at my article «Set your hostname in Linux».
DNS Address(es)
There is no actual command to see your DNS addresses. You don’t really need one. All you need to do is examine the /etc/resolv.conf file with the command less /etc/resolv.conf, at whichpoint you will see something like:
Gateway address
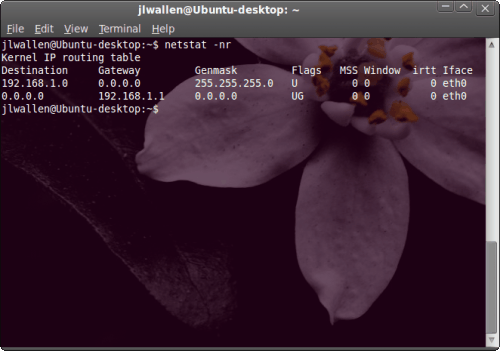
Now let’s find out what the Gateway address is. The command used for this is the netstat command. This command does quite a bit more than just discover your gateway. What the netstat command does is print network connections, routing tables, interface statistics, masquerade connections, and multicast memberships. But to find the gateway address you would issue the command netstat -nr and you will see something like that shown in Figure 2. You can probably guess it, but the Gateway address is 192.168.1.1. The flags you used in that command are n (for numeric addresses) and r (for route).
Of course the netstat command can do much more than that (we’ll cover that in another article).
Final thoughts
Yes, there are a lot of tools that can be used in Linux. It all depends upon how you want to get your information. In both the GNOME and KDE desktops there are outstanding GUI tools you can use for all of this. But knowing the command line route makes you much more versatile.
Источник
14 Useful Linux Networking Commands
Geekflare is supported by our audience. We may earn affiliate commissions from buying links on this site.
Configuring, monitoring, and securing networks form an essential part of a Sysadmin’s job. When it comes to managing Linux networks, there are many commands and utilities available.
At times networked systems fail. You as an administrator are required to diagnose and resolve issues. Monitoring helps in detecting problems and fixing them before things get out of hand. Monitoring for security and performance also forms an essential part of an admin’s activities.
Here we discuss some commonly used commands to manage Linux networks.
The iproute2 package includes the IP command which is used for network and routing configuration. This replaces the traditional ifconfig and route commands.
ip takes a second argument that specifies the object on which you wish to execute a command and an action like add, delete, or show.
ip link
ip link is for configuring, adding, and deleting network interfaces. Use ip link show command to display all network interfaces on the system :
You can see the man page for ip link with:
ip address
Use ip address command to display addresses, bind new address or delete old ones. The man page ip address command is named as ip-address.
For example, the following command shows the IP address assigned to the network interface enp0s8:
ip route
Use the IP route to print or display the routing table. The following command displays the contents of the routing table:
While Nmap had been used in many movies, The Matrix Reloaded ( Wikipedia , IMDB , Amazon ) turned Nmap into a movie star!.
Nmap (“Network Mapper”) is a powerful utility used for network discovery, security auditing, and administration. Many system admins use it to determine which of their systems are online, and also for OS detection and service detection.
The default Nmap scan shows the ports, their state (open/closed), and protocols. It sends a packet to 1000 most common ports and checks for the response.
To check which hosts on your network are up:
Use -O flag to identify which operating system a host is running.
A word of caution: Nobody appreciates their systems being scanned over the internet. So before you do so, seek permission.
You can also use Nmap on Windows, check out this installation guide.
Use ping to see if a host is alive. This super simple command helps you check the status of a host or a network segment. Ping command sends an ICMP ECHO_REQUEST packet to the target host and waits to see if it replies.
However, some hosts block ICMP echo requests with a firewall. Some sites on the internet may also do the same.
By default, ping runs in an infinite loop. To send a defined number of packets, use -c flag.
With -o flag ping exits successfully after receiving one reply packet.
You can use -n flag to avoid reverse DNS lookups. The ICMP sequence number is particularly important. A Break in sequence numbers indicates lost packets.
A failed ping could be due to
- network failure
- host being not alive
- firewall blocking ICMP ECHO requests
You can also perform an online ping test to check the connectivity from different parts of the world.
iPerf
While ping verifies the availability of a host, iPerf helps analyze and measure network performance between two hosts. With iPerf, you open a connection between two hosts and send some data. iPerf then shows the bandwidth available between the two hosts.
You can install an iPerf using your distribution package manager. For example on Ubuntu-based distributions you can install like this:
Once you have installed iPerf on both the machines, start the iPerf server on one of them. The following example starts the iPerf server on a host with IP address 10.0.0.51.
On the second machine start iPerf with the -c flag. This connects with the server and sends some data.
iPerf returns with the bandwidth results in a few seconds.
traceroute
If ping shows missing packets, you should use traceroute to see what route the packets are taking. Traceroute shows the sequence of gateways through which the packets travel to reach their destination. For example, traceroute from my machine to google.com shows the following:
Line 4 in this output shows a * in the round trip times. This indicates no response was received. This can be due to many reasons – as the traceroute ICMP packets are low-priority, these may be dropped by a router. Or there could be simply congestion. If you see a * in all the time fields for a given gateway, then possibly the gateway is down.
Many web-based route tracing tools allow you to do a reverse traceroute, that is, from a website to your host. You can check these at traceroute.org or Geekflare Traceroute.
tcpdump
tcpdump is a packet sniffing tool and can be of great help when resolving network issues. It listens to the network traffic and prints packet information based on the criteria you define.
For example, you can examine all packets sent to or from a particular host, Ubuntu18 in this example:
By default, tcpdump resolves IP addresses to hostnames. Use -n flag, if you do not want tcpdump to perform name lookups.
tcpdump output prints one line for each packet. Use -c flag to limit output, 5 in the example above.
tcpdump is useful for solving network problems and also identifying potential problems. It is a good idea to run a tcpdump on your network occasionally to verify everything is in order.
netstat
Netstat command is used to examine network connections, routing tables, and various network settings and statistics.
Use -i flag to list the network interfaces on your system.
Here is an example:
Using -r flag will display the routing table. This shows the path configured for sending network packets.
An asterisk in the last two lines indicates that no gateway is required to send packets to any host on these networks. This host is directly connected to the networks 10.0.0.0 and 10.0.2.0.
In the first line, the destination is the default, which means any packet destined for a network not listed in this table is handled by the router 10.0.2,2.
netstat command without any options displays a list of open sockets. Use -l flag to show only listening sockets, which by default, are not shown. You can use -a flag to show listening and non-listening sockets. Here is an example:
More Netstat command example here
Linux installations have a lot of services running by default. These should be disabled or preferably removed, as this helps in reducing the attack surface. You can see what services are running with the netstat command. While netstat is still available, most Linux distributions are transitioning to ss command.
use ss command with -t and -a flags to list all TCP sockets. This displays both listening and non-listening sockets.
To display only TCP connections with state established:
ssh enables you to connect securely with remote hosts over the internet. Earlier rlogin and telnet were used to connect to and administer remote hosts. However, both suffer from a fundamental flaw, that is, they send all information including login names and passwords in cleartext.
ssh enables secure communication over the internet with the following two features :
- It confirms that the remote host is, who it says it is.
- It encrypts all communication between the hosts.
To connect to a remote host you need to have an OpenSSH server running on the remote host. You can install it using your distribution package manager. For example on Ubuntu you can install it like this:
Here is an example showing how you can connect to the remote host 10.0.0.50 using the ssh command:
You get a message saying that the authenticity of the host 10.0.0.50 cannot be established, this is because it’s the first time a connection is being made with 10.0.0.50 (server) and the ssh client has never seen this remote host before. Enter yes to continue connecting. Once the connection has been established, you are prompted for a password:
After you enter the correct password, you are logged into the remote host.
You can exit this remote shell with the exit command.
Also, you can easily execute a single command on the remote host using ssh. For example, to run df -h on the remote host:
scp and sftp
scp (secure copy) is very similar to cp command for copying files, with an addition – you can include remote hostnames in the source or destination pathnames. The hostname and the directory path are separated by a colon. This enables you to copy files securely over the network in an encrypted form. The following command copies a.txt from the local machine to 10.0.0.50 :
sftp (secure ftp) is also a file copy program similar to ftp . However, it uses an SSH encrypted tunnel to copy files, instead of sending everything in cleartext. Also, you do not need an FTP server running on the remote host. You only need an ssh server. Here is an example session:
Ifconfig
Mostly we use ifconfig command to check the IP address assigned to the system.
dig (Domain Information Groper) is a flexible tool for interrogating DNS name servers.
It performs DNS lookups and displays the answers that are returned from the name servers.
telnet
telnet connect destination’s host and port via a telnet protocol if a connection establishes means connectivity between two hosts is working fine.
nslookup
nslookup is a program to query domain name servers and resolving IP.
Summary
Networking in Linux is a vast subject, with a large number of commands and utilities. In this article, we have discussed some commonly used commands which hopefully, will help you in managing and securing your network.
Источник
Linux – Network Information Service
The Network Information Service, or NIS (initially called YP or yellow pages), is a mainframe-client index service convention for circulating server configuration information, for example, client and host names between PCs on a PC network. Sun Microsystems built up the NIS; the innovation is authorized to essentially all other Unix merchants. Since British Telecom PLC claimed the name “Yellow Pages” as an enlisted brand name in the United Kingdom for its paper-based, business phone catalog, Sun changed the name of its framework to NIS, however, all the orders capacities actually start with “yp”. A NIS/YP framework keeps up and disseminates a focal index of the client and gathering information, hostnames, email pseudonyms, and other content-based tables of information in a PC network. For instance, in a typical UNIX climate, the rundown of clients for ID is put in/and so forth/passwd and mystery verification hashes in/and so on/shadow. NIS includes another “worldwide” client list which is utilized for recognizing clients on any customer of the NIS area. Administrators can arrange NIS to serve secret key information to outside cycles to verify clients utilizing different variants of the Unix crypt(3) hash calculations. In any case, in such cases, any NIS(0307) customer can recover the whole secret phrase information base for disconnected investigation. Kerberos was intended to deal with confirmation in a safer way.
We utilize the Linux NIS mainframe (Network Information Service) for sharing basic information put away in level documents between frameworks on a network. It is frequently ideal to have a mutual archive, (for example, NIS) for putting away clients and gatherings information as opposed to putting away them in level documents like/and so forth/passwd. So what is the advantage of that? By making such documents accessible through the NIS worker, that would permit any distant NIS customer machine to access or question the information in these mutual records and use them as expansions to the nearby forms.
NIS isn’t for sharing records. We can share any even document which in any event has one section with an extraordinary worth by means of NIS like/and so on/services record. The primary advantage of utilizing the NIS worker is that you keep your information and records, and spread any updates to all clients. A few clients, particularly Windows clients, may think this is a kind of Active Directory like service. The Linux NIS worker is more established than Active Directory and not a reproduce for it.
NIS Introduction:
By running NIS, the framework administrator can disperse administrative information bases, called maps, among an assortment of mainframes (ace and slaves). The administrator can refresh those information bases from a brought together area in a programmed and solid design to guarantee that all customers share a similar naming service information predictably all through the network. NIS was grown freely of DNS and has a marginally extraordinary core interest. While DNS centers around making correspondence less difficult by utilizing machine names rather than mathematical IP addresses, NIS centers around making network administration more sensible by giving unified command over an assortment of network information. NIS stores information about machine names and addresses, yet additionally about clients, the network itself, and network services. This assortment of network information is alluded to as the NIS namespace.
Note — In certain settings machine names are alluded to have had names or machine names. This conversation utilizes a machine, yet some screen messages or NIS map names may utilize host or machine.
NIS Architecture:
NIS utilizes a customer worker plan. NIS mainframes offer types of assistance to NIS customers. The primary workers are called ace workers, and for unwavering quality, they have reinforcement or slave workers. Both ace and slave workers utilize the NIS information recovery programming and both store NIS maps. NIS utilizes domains to mastermind the machines, clients, and networks in its namespace. Nonetheless, it doesn’t utilize an area chain of command; a NIS namespace is level.
A NIS domain can’t be associated straightforwardly to the Internet utilizing just NIS. Notwithstanding, associations that need to utilize NIS and furthermore be associated with the Internet can consolidate NIS with DNS. You can utilize NIS to deal with all neighborhood information and use DNS for the Internet to have queries. NIS gives a sending service that advances have queries to DNS if the information can’t be found in a NIS map. The Solaris working climate additionally permits you to set up the nsswitch.conf record with the goal that has query demands go just to DNS, or to DNS and afterward NIS on the off chance that not found by DNS, or to NIS and afterward DNS if not found by NIS.
NIS Machine Types: There are three kinds of NIS machines:
- Ace mainframe
- Slave mainframe
- Customers of NIS mainframes
Any machine can be a NIS customer, however, just machines with plates ought to be NIS workers, either ace or slave. Workers are likewise customers, ordinarily of themselves.
NIS Servers:
The NIS mainframe doesn’t need to be a similar machine as the NFS record worker. NIS mainframes come in two assortments, ace, and slave. The machine assigned as ace worker contains the arrangement of guides that the framework administrator makes and updates as important. Every NIS space must have one, and just one, ace worker, which can engender NIS refreshes with the least presentation debasement. We can assign extra NIS workers in the domain as slave workers. A slave worker has a total duplicate of the ace arrangement of NIS maps. At whatever point the ace worker maps are refreshed, the updates are proliferated among the slave workers. Slave workers can deal with any flood of solicitations from the ace worker, limiting “worker inaccessible” mistakes.
Ordinarily, the framework administrator assigns one ace worker for all NIS maps. Be that as it may, on the grounds that every individual NIS map has the machine name of the ace worker encoded inside it, you could assign various workers to go about as ace and slave workers for various guides. To limit disarray, assign a solitary worker as the ace for all the guides you make inside a solitary area. The models in this part expect that one worker is the ace for all guides in the space.
NIS Clients:
NIS customers run measures that demand information from maps on the workers. Customers don’t make a differentiation among ace and slave workers, since all NIS workers ought to have a piece of similar information.
NIS Elements:
The NIS naming service is made out of the accompanying components:
- Domains
- Guides
- Daemons
- Utilities
- NIS Command Set
The NIS is an information base that contains a progression of tables. It makes tables from text records like/and so on/passwd,/and so forth/services, and some other plain documents. Each table may contain one section or more with a novel key on each line. You can consider it like any typical information base. You can question these tables in two different ways:
- Posting the whole table
- Pulling a particular passage via looking
At the point when a program solicitations to look for a client secret phrase subtleties, the customer checks the/and so on/passwd record to check on the off chance that the client doesn’t exist there; the customer at that point approaches the NIS worker to look for it in the/and so on/passwd table from the NIS worker. You can utilize any of the services and applications that accompany the NIS mainframe:
- ypserv: This service sits tight for inquiries and offers responses to NIS customers.
- ypbind: This is the customer side of NIS.
- ypxfrd: You can utilize this service for sending the NIS information bases from ace MIS workers to slave workers.
The NIS Domain: A NIS domain is an assortment of machines that share a typical arrangement of NIS maps. Every space has an area name and each machine sharing the basic arrangement of guides has a place with that area. Any machine can have a place with a given area, as long as there is a mainframe for that space’s guides in a similar network. A NIS customer machine acquires its area name and ties to a NIS worker as a component of its boot cycle.
Five daemons are utilized in order to provide the NIS service:
| Daemon | Function |
|---|---|
| ypserv | Server process |
| ypbind | Binding process |
| ypxfrd | High-speed map transfer |
| rpc.yppasswdd | NIS password update daemon |
| rpc.ypupdated | Modifies other maps such as publickey |
A total of 9 utilities support the NIS service:
| Utility | Function |
|---|---|
| makedbm | Makes dbm record for a NIS map |
| ypcat | Records information in a guide |
| ypinit | Fabricates and introduces a NIS information base and instates NIS customer’s ypservers list |
| ypmatch | Finds a particular passage in a guide |
| yppoll | Gets a guide request number from a worker |
| yppush | Proliferates information from NIS ace to NIS slave worker |
| ypset | Sets binding to a specific mainframe |
| ypwhich | Records name of the NIS mainframe and alias interpretation table |
| ypxfr | Moves information from ace to slave NIS mainframe |
Applications of NIS:
There are some valuable apparatuses that can assist you with dealing with the information in the information base.
- ypcat: You can utilize this to get information from the NIS worker by separating it from the NIS map.
- ypwhich: gets the name of the Linux NIS worker that is reacting to your solicitations.
- ypmatch: instead of snatching the whole guide, or you can look by key to get a particular section.
Источник