- Top 10 Kali Linux Tools For Hacking
- 1. Nmap
- 2. Burp Suite
- 3. Wireshark
- 4. metasploit Framework
- 5. aircrack-ng
- 7. John the Ripper
- 8. sqlmap
- 9. Autopsy
- 10. Social Engineering Toolkit
- Ethical Hacking using Kali Linux — A Beginner’s Guide To Kali Linux
- What is Kali Linux?
- Development of Kali Linux
- Why Use Kali Linux?
- System Requirements for Kali Linux
- List of Tools
- Aircrack-ng
- THC Hydra
- Nessus
- WireShark
- Demonstration of Power: Aircrack-ng and Crunch
Top 10 Kali Linux Tools For Hacking
Kali Linux is a Debian-derived Linux distribution that is maintained by Offensive Security. It was developed by Mati Aharoni and Devon Kearns. Kali Linux is a specially designed OS for network analysts, Penetration testers, or in simple words, it is for those who work under the umbrella of cybersecurity and analysis.
The official website of Kali Linux is Kali.org. It gained its popularity when it was practically used in Mr. Robot Series. It was not designed for general purposes, it is supposed to be used by professionals or by those who know how to operate Linux/Kali. To know how to install Kali Linux check its official documentation.
Sometimes we have to automate our tasks while performing penetration testing or hacking as there could be thousands of conditions and payloads to test and testing them manually is a difficult task, So to increase the time efficiency we use tools that come pre-packed with Kali Linux. These tools not only saves our time but also captures the accurate data and output the specific result. Kali Linux comes packed with more than 350 tools which could be useful for hacking or penetration testing. Here we have the list of important Kali Linux tools that could save a lot of your time and effort.
1. Nmap
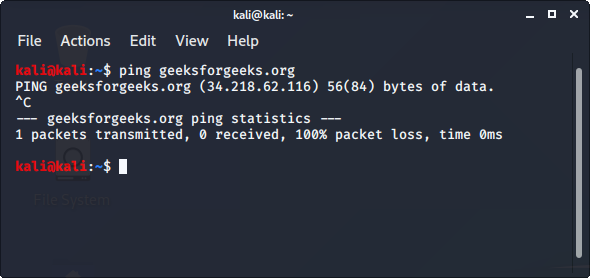
Nmap is an open-source network scanner that is used to recon/scan networks. It is used to discover hosts, ports, and services along with their versions over a network. It sends packets to the host and then analyzes the responses in order to produce the desired results. It could even be used for host discovery, operating system detection, or scanning for open ports. It is one of the most popular reconnaissance tools.
To use nmap:
- Ping the host with ping command to get the IP address
- Open the terminal and enter the following command there:
- Replace the IP address with the IP address of the host you want to scan.
- It will display all the captured details of the host.
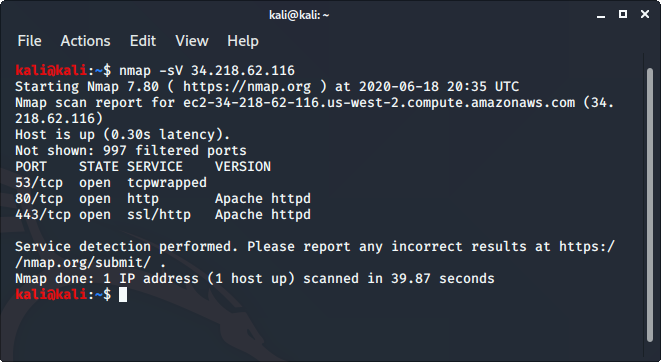
To know more, you can read more from here .
2. Burp Suite
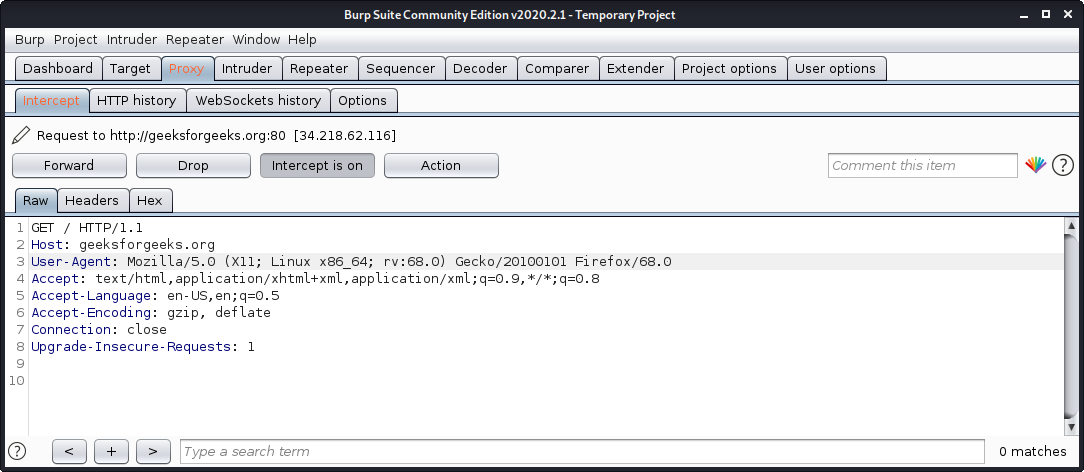
Burp Suite is one of the most popular web application security testing software. It is used as a proxy, so all the requests from the browser with the proxy pass through it. And as the request passes through the burp suite, it allows us to make changes to those requests as per our need which is good for testing vulnerabilities like XSS or SQLi or even any vulnerability related to the web.
Kali Linux comes with burp suite community edition which is free but there is a paid edition of this tool known as burp suite professional which has a lot many functions as compared to burp suite community edition.
To use burpsuite:
- Read this to learn how to setup burp suite.
- Open terminal and type “burpsuite” there.
- Go to the Proxy tab and turn the interceptor switch to on.
- Now visit any URL and it could be seen that the request is captured.
3. Wireshark
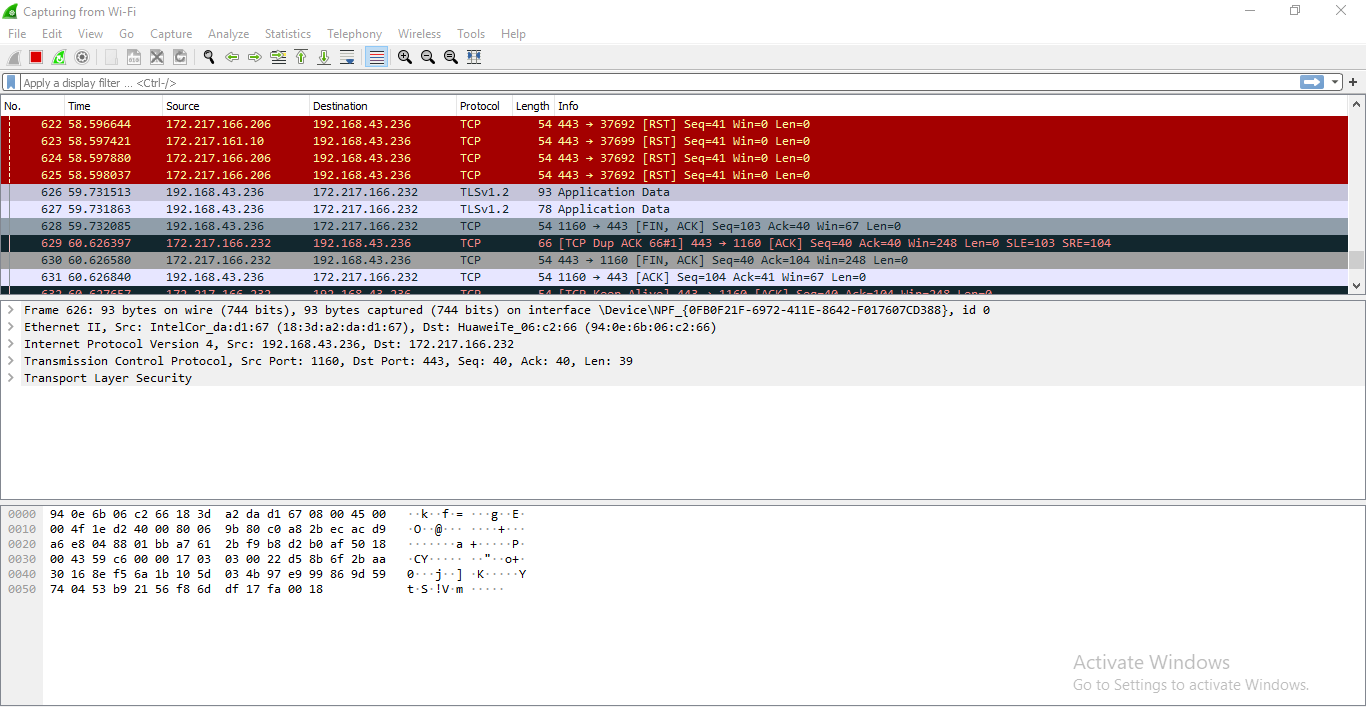
Wireshark is a network security tool used to analyze or work with data sent over a network. It is used to analyze the packets transmitted over a network. These packets may have information like the source IP and the destination IP, the protocol used, the data, and some headers. The packets generally have an extension of “.pcap” which could be read using the Wireshark tool. Read thisto learn how to set up and configure Wireshark.
To use wireshark:
- Open Wireshark and download a demo pcap file from here
- Press”ctrl+o” to open a pcap file in wireshsark.
- Now it can be seen that it display the list of packets along with the headers of these packets.
4. metasploit Framework
Metasploit is an open-source tool that was designed by Rapid7 technologies. It is one of the world’s most used penetration testing frameworks. It comes packed with a lot of exploits to exploit the vulnerabilities over a network or operating systems. Metasploit generally works over a local network but we can use Metasploit for hosts over the internet using “port forwarding“. Basically Metasploit is a CLI based tool but it even has a GUI package called “armitage” which makes the use of Metasploit more convenient and feasible.
To use metasploit:
- Metasploit comes pre-installed with Kali Linux
- Just enter “msfconsole” in the terminal.

5. aircrack-ng
Aircrack is an all in one packet sniffer, WEP and WPA/WPA2 cracker, analyzing tool and a hash capturing tool. It is a tool used for wifi hacking. It helps in capturing the package and reading the hashes out of them and even cracking those hashes by various attacks like dictionary attacks. It supports almost all the latest wireless interfaces.
To use aircrack-ng:
- aircrack-ng comes pre-compiled with Kali Linux.
- Simply type aircrack-ng in the terminal to use it.
6. Netcat
Netcat is a networking tool used to work with ports and performing actions like port scanning, port listening, or port redirection. This command is even used for Network Debugging or even network daemon testing. This tool is considered as the Swiss army knife of networking tools. It could even be used to do the operating related to TCP, UDP, or UNIX-domain sockets or to open remote connections and much more.
To use netcat:
- Netcat comes pre-installed with Kali Linux.
- Just type “nc” or “netcat” in the terminal to use the tool.
- To perform port listening type the following commands in 2 different terminals.

Read this for more information ragarding netcat tool.
7. John the Ripper
John the Ripper is a great tool for cracking passwords using some famous brute for attacks like dictionary attack or custom wordlist attack etc. It is even used to crack the hashes or passwords for the zipped or compressed files and even locked files as well. It has many available options to crack hashes or passwords.
To use John the Ripper:
- John the ripper comes pre-installed in Kali Linux.
- Just type “john” in the terminal to use the tool.
8. sqlmap
sqlmap is one of the best tools to perform SQL injection attacks. It just automates the process of testing a parameter for SQL injection and even automates the process of exploitation of the vulnerable parameter. It is a great tool as it detects the database on its own so we just have to provide a URL to check whether the parameter in the URL is vulnerable or not, we could even use the requested file to check for POST parameters.
To use sqlmap tool:
- sqlmap comes pre-installed in Kali Linux
- Just type sqlmap in the terminal to use the tool.
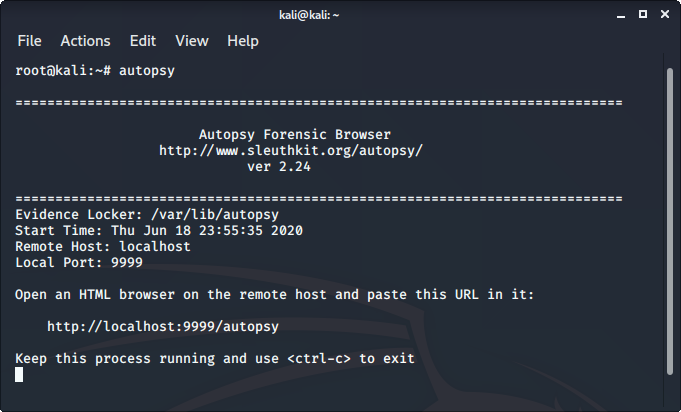
9. Autopsy
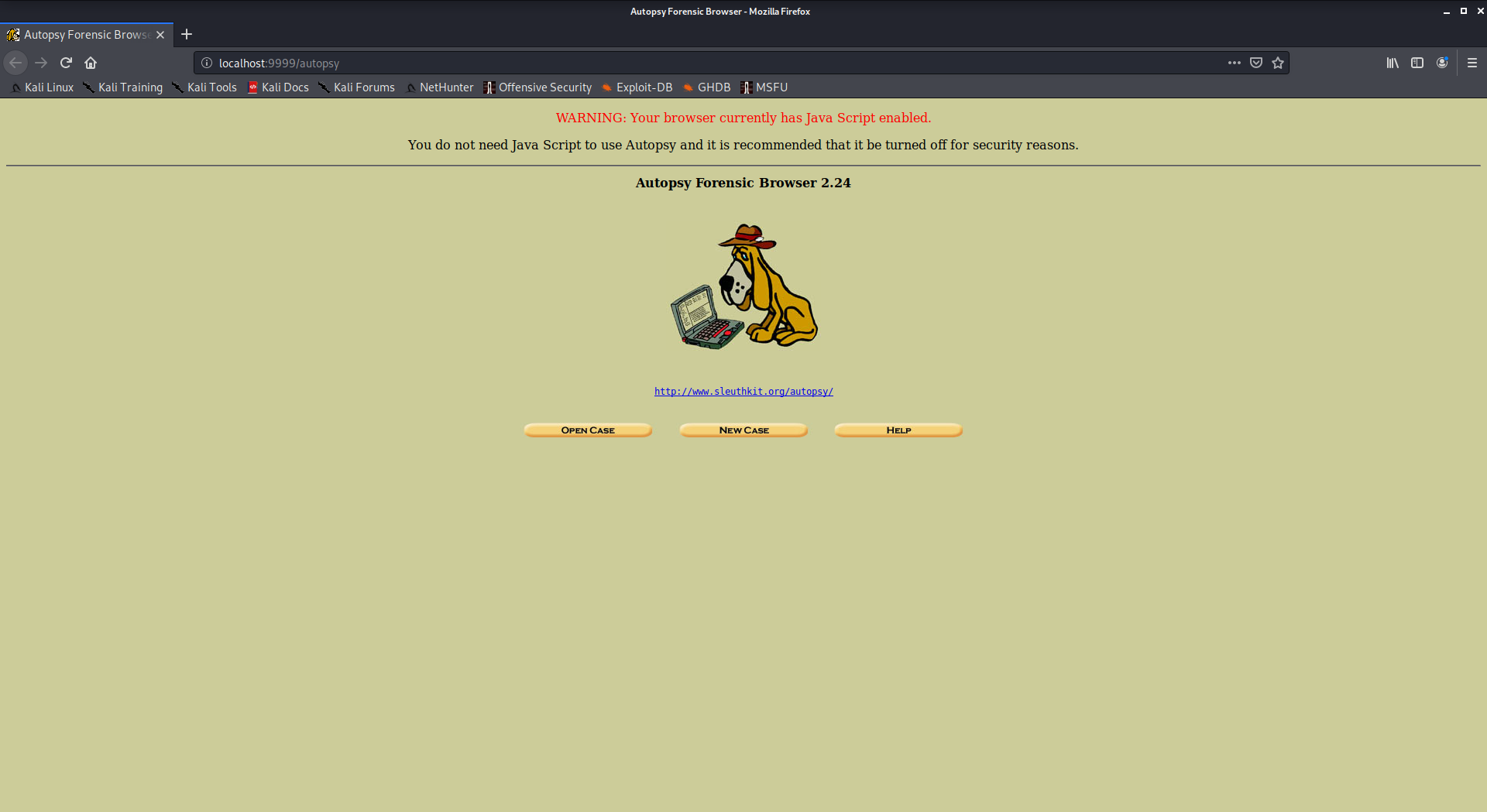
Autopsy is a digital forensics tool that is used to gather the information form forensics. Or in other words, this tool is used to investigate files or logs to learn about what exactly was done with the system. It could even be used as a recovery software to recover files from a memory card or a pen drive.
To use autopsy tool:
- Autopsy comes pre-installed in Kali Linux
- Just type “autopsy” in the terminal.
- Now visit http://localhost:9999/autopsy in order to use the tool.
10. Social Engineering Toolkit
Social Engineering Toolkit is a collection of tools that could be used to perform social engineering attacks. These tools use and manipulate human behavior for information gathering. it is a great tool to phish the websites even.
To use Social Engineering Toolkit
- Social Engineering Toolkit comes pre-installed with Kali Linux
- Just type “setoolkit” in the terminal.
- Agree to the terms and conditions to start using the social engineering toolkit.
Источник
Ethical Hacking using Kali Linux — A Beginner’s Guide To Kali Linux
More often than not, specific operating systems get tied to certain tasks. Anything related to graphics or content creation brings up macOS in our mind. Similarly, any instance of hacking or just generally fiddling around with network utilities is also mapped to a particular operating system and that is Kali Linux. In this article, I’ll be writing a general introduction to Kali Linux and how it can be used for ethical hacking. The following topics are discussed in this write up regarding ‘Ethical Hacking Using Kali Linux’:
- What is Kali Linux?
- Development of Kali Linux
- Why Use Kali Linux?
- System Requirements for Kali Linux
- List of Tools
- Demonstration of Power — aircrack-ng and crunch
What is Kali Linux?
Kali Linux is a Debian-based Linux distribution. It is a meticulously crafted OS that specifically caters to the likes of network analysts & penetration testers. The presence of a plethora of tools that come pre-installed with Kali transforms it into an ethical hacker’s swiss-knife. Previously known as Backtrack, Kali Linux advertises itself as a more polished successor with more testing-centric tools, unlike Backtrack which had multiple tools that would serve the same purpose, in turn, making it jampacked with unnecessary utilities. This makes ethical hacking using Kali Linux a simplified task.
Development of Kali Linux
Mati Aharoni and Deavon Kearns are the core developers of Kali Linux. It was a rewrite of Backtrack Linux, which was another penetration testing centric Linux distribution. The development of Kali is set according to the Debian standards as it imports the majority of its code from Debian repositories. The development began in early March 2012, amongst a small group of developers. Only a very selected few developers were allowed to commit packages, that too in a protected environment. Kali Linux came out of development with its first release in 2013. Since then, Kali Linux has been through a number of major updates. The development of these updates is handled by Offensive Security.
Why Use Kali Linux?
There are a wide array of reasons as to why one should use Kali Linux. Let me list down a few of them:
- As free as it can get — Kali Linux has been and will always be free to use.
- More tools than you could think of — Kali Linux comes with over 600 different penetration testing and security analytics related tool.
- Open-source — Kali, being a member of the Linux family, follows the widely appreciated open-source model. Their development tree is publicly viewable on Git and all of the code is available for your tweaking purposes.
- Multi-language Support — Although penetration tools tend to be written in English, it has been ensured that Kali includes true multilingual support, allowing more users to operate in their native language and locate the tools they need for the job.
- Completely customizable — The developers at offensive security understand that not everyone will agree with their design model, so they have made it as easy as possible for the more adventurous user to customize Kali Linux to their liking, all the way down to the kernel.
System Requirements for Kali Linux
Installing Kali is a piece of cake. All you have to make sure is that you have the compatible hardware. Kali is supported on i386, amd64, and ARM (both ARMEL and ARMHF) platforms. The hardware requirements are minimal as listed below, although better hardware will naturally provide better performance.
- A minimum of 20 GB disk space for the Kali Linux install.
- RAM for i386 and amd64 architectures, minimum: 1GB, recommended: 2GB or more.
- CD-DVD Drive / USB boot support/ VirtualBox
List of Tools
Below is a list of tools that come pre-installed for ethical hacking using Kali Linux. This list is by no means expansive as Kali has a plethora of tools, all of which cannot be listed and explained in one article.
Aircrack-ng
Aircrack-ng is a suite of tools used to assess WiFi network security. It focuses on key areas of WiFi security:
- Monitoring: Packet capture and export of data to text files for further processing by third-party tools.
- Attacking: Replay attacks, de-authentication, fake access points, and others via packet injection.
- Testing: Checking WiFi cards and driver capabilities (capture and injection).
- Cracking: WEP and WPA PSK (WPA 1 and 2).
All tools are command line which allows for heavy scripting. A lot of GUIs have taken advantage of this feature. It works primarily Linux but also Windows, OS X, FreeBSD, OpenBSD, NetBSD, as well as Solaris.
Network Mapper, also commonly known as Nmap, is a free and open source utility for network discovery and security auditing. Nmap uses raw IP packets in stealthy ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
Many systems and network administrators also find it useful for tasks like:
- network inventory
- managing service upgrade schedules
- monitoring host or service uptime
THC Hydra
When you need to brute force crack a remote authentication service, Hydra is often the tool of choice. It can perform rapid dictionary attacks against more than 50 protocols, including telnet, FTP, HTTP, HTTPs, SMB, several databases, and much more. it can be used to crack into web scanners, wireless networks, packet crafters, etc.
Nessus
Nessus is a remote scanning tool that you can use to check computers for security vulnerabilities. It does not actively block any vulnerabilities that your computers have but it will be able to sniff them out by quickly running 1200+ vulnerability checks and throwing alerts when any security patches need to be made.
WireShark
WireShark is an open-source packet analyzer that you can use free of charge. With it, you can see the activities on a network from a microscopic level coupled with pcap file access, customizable reports, advanced triggers, alerts, etc. It is reportedly the world’s most widely-used network protocol analyzer for Linux.
Demonstration of Power: Aircrack-ng and Crunch
Step 1: Check the name of your wireless interface and put it into monitor mode.
Step 2: Kill any processes that might interfere with the scan process. Always kill network administrator first. You might need to run the shown command more than once.
Step 3: After you have successfully killed all process, run the command — airodump-ng . It should produce a list of access points as shown below:
Step 4: Choose the access point and run it along with the -w flag to write the result into a file. Our file is called capture.
Step 5: Running the above command should show you the MAC address of the devices connected to that access point under ‘stations’.
Step 6 — This is the most important step in ethical hacking using Kali Linux. Here we will broadcast a de-authentication signal to the access point we have chosen to attack. This disconnects the devices connected to the access point. Since these devices will most likely have the password stored they will try to auto reconnect. This will start a 4-way handshake between the device and the access point and will be captured in the scan going on from step 4 (yes, that scan is still running in the background).
Step 7: Now we will use crunch along with aircrack-ng. Crunch is a wordlist generator. This process to crack passwords assumes you know a little about the password, for example, the length, some specific characters etc. The more you know the faster the process. Here I have tried to generate a list of words that begin with ‘sweetship’ as I know that password contains that phrase. The result is piped into the aircrack command which takes the capture files and compares the key values.
Step 8: The scan results should look something like this depending on the parameters you have input.
Step 9: When the password is matched. It shows it in the bracket following ‘key found’.
This brings us to the end of our article on Ethical Hacking using Kali Linux. I hope you found this article informative and added value to your knowledge. If you wish to check out more articles on the market’s most trending technologies like Artificial Intelligence, DevOps, Cloud, then you can refer to Edureka’s official site.
Do look out for other articles in this series which will explain the various other aspects of Ethical Hacking.
Источник