- Linux Check User Password Expiration Date and Time
- Linux check user password expiration using chage
- View account again information on Linux
- Check the user account password expiry information on Linux
- Change password expiry date
- Set expire date
- Set warning for the user before password expires
- Conclusion
- How to check last password change date of user in Linux/Unix
- chage command
- Check last password change date
- For system user
- Understanding shadow file format and fields.
- For Active Directory User
- Check password expiration in Linux
- passwd command
- Check password status
- Related Posts
- How To Check The Password Complexity In Linux
- Check The Password Complexity In Linux
- HowTo: Linux Check Password Strength With Cracklib-check Command
- Creating a strong and unique password for Linux or Unix-like systems
- Install cracklib on a Linux based system
- Say hello to cracklib-check
- Examples
- A note about security
- Как проверить пароль в Linux?
Linux Check User Password Expiration Date and Time
Linux check user password expiration using chage
- Open the terminal application
- Type chage -l userName command to display password expiration information for Linux user account.
- The -l option passed to the change show account aging information.
- Check tom user’s password expiry time, run: sudo chage -l tom
Let us see some examples and usage information in details.
View account again information on Linux
To see account aging information such as expiry date and time, enter:
To see account aging info for usernamed vivek, enter:
$ chage -l vivek
Sample outputs:
The above outputs indicates that password aging disabled.
Check the user account password expiry information on Linux
Let us try one more example:
$ sudo chage -l raj
Sample outputs:
It seems that user account scheduled to expire on 01/Jan/2013. You can use the grep command to filter out info too:
$ sudo chage -l raj | grep ‘Password expires’
Change password expiry date
You can set the maximum number of days during which a password is valid. For example, make sure password is valid for 90 days for user named jerry:
sudo chage -M 90 jerry
sudo chage -l jerry
Please note that passing the number -1 will remove checking a password’s validity:
sudo chage -M -1 tom
You can also set the minimum number of days between password changes:
sudo chage -m 30 jerry
However, a value of zero indicates that the user may change his/her password at any time:
sudo chage -m 0 marlena
Set expire date
The syntax is:
sudo chage -E EXPIRE_DATE userName
One can set the date or number of days since January 1, 1970 on which the user’s account will no longer be accessible. The date may also be expressed in the format YYYY-MM-DD (or the format more mmonly used in your area). A user whose account is locked must contact the system administrator before being able to use the system again.
sudo chage -E 2020-03-31 sai
Passing the number -1 as the EXPIRE_DATE will remove an account expiration date:
sudo chage -E -1 tristan
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
Set warning for the user before password expires
Try using the following syntax to set the number of days of warning before a password change is required:
sudo chage -W WARN_DAYS userName
sudo chage -W 30 raj
The WARN_DAYS option is the number of days prior to the password expiring that a user will be warned his/her password is about to expire. Verify info with following command:
sudo chage -l raj
Conclusion
The chage command changes the number of days between password changes and the date of the last password change. The same command also check user password expiration date and time on Linux. See chage man page for more information here.
🐧 Get the latest tutorials on Linux, Open Source & DevOps via
Источник
How to check last password change date of user in Linux/Unix
Table of Contents
In this article I will cover below topics:
- chage command examples
- check last password change date of system and Active Directory User
- check password status of user
- overview on /etc/shadow file format and field
- check password expiration
chage command
The chage command changes the number of days between password changes and the date of the last password change. This information is used by the system to determine when a user must change their password. It uses /etc/passwd and /etc/shadow to get user’s password related details such as to check last password change date, password expiry and aging related information.
Check last password change date
For system user
chage command reads last password change date from file /etc/shadow . The date of last password change is stored in 3rd field in file /etc/shadow
To view account aging information for user deepak using chage command
Understanding shadow file format and fields.
The information is stored not exactly as date+time but as number of days since Jan 1, 1970. Example given below.
We have 9 fields in /etc/shadow. The meanings of each field in the order they are present:
- sp_namp — pointer to null-terminated user name
- sp_pwdp — pointer to null-terminated password
- sp_lstchg — days since Jan 1, 1970 password was last changed
- sp_min — days before which password may not be changed
- sp_max — days after which password must be changed
- sp_warn — days before password is to expire that user is warned of pending password expiration
- sp_inact — days after password expires that account is considered inactive and disabled
- sp_expire — days since Jan 1, 1970 when account will be disabled
- sp_flag — reserved for future use
As you see the fist section can be used to check last password change date of user
But the downside here is that root user can also change last password change date using » -d «. Here I change user deepak’s last password change date to 23rd Nov 2019
Next check last password change date for user deepak
For Active Directory User
But what if your Linux system is connected to Windows Active Directory , so to check last password change date of AD user you will need access to the Windows Active Directory node. I am not aware of any tool which can show last password change related details of an Active Directory user on Linux .
Please do let me know via comment section if you are familiar with any tool. On Windows AD you can use » net user » using powershell to check when password expires for AD user.
Syntax:
I have an AD user amit on my RHEL 7 Linux client which is connected to Windows Active Directory
For example to check last password change date of Active Directory user amit , from the powershell CLI of Windows Server 2012
Check password expiration in Linux
Using chage command you can also check password expiration date of a user in Linux, and of course change it. Now to check password expiration date of user deepak
So now the password is set to » never expire » for deepak . To change password expiration date of user deepak we will use » -M «. Using -M we wet the maximum number of days during which a password is valid. So here we set password expiration after 30 days
Now check password expiration date of deepak
passwd command
We have another tool passwd command in Linux which most of us mostly use to change password of user. But passwd command can do much more such as, check password status , reset password’s failed login attempts , lock and unlock user and many more.
Check password status
You can also check password status of user with passwd command. Here -S will output a short information about the status of the password for a given account
You can also check last password change date of a user using » passwd -S «. Observe the third field of below output to check last password change date of the provided user above which is in synch with chage command output from the same Linux machine.
In case the password is locked for user deepak , the check password status output would be like below
Lastly I hope the steps from the article to check last password change date and password aging information of system and active directory user in Linux was helpful. So, let me know your suggestions and feedback using the comment section.
Related Posts
Didn’t find what you were looking for? Perform a quick search across GoLinuxCloud
If my articles on GoLinuxCloud has helped you, kindly consider buying me a coffee as a token of appreciation.

For any other feedbacks or questions you can either use the comments section or contact me form.
Thank You for your support!!
Источник
How To Check The Password Complexity In Linux
We already posted a brief guide about — how to generate a strong password in Linux a while ago. Now, we are going to find out if the generated password is really strong or not. In this short tutorial, we will see how to check the password complexity in Linux from commandline. Before going further, here are some useful tips to all those who wants to keep their system safe.
- Never ever use the same password for different Email accounts, ssh/ftp/sftp logins. If a hacker managed to crack your password, s/he literally have access to all accounts. So, generate and use different unique password for each account.
- A good password should be the combination of letters, numbers, special characters.
- Make sure your password has at least 12 or more characters. Check our guide how to force users to use strong password.
- Don’t save your passwords online. Use good password manager or memorize them.
- Consider two factor authentication if possible.
- More importantly, don’t use valid answers for security questions, eventually with enough data breaches, hackers will have all the answers. The common security questions are father’s maiden name, school name, favorite pet’s name, last name of first girlfriend/boyfriend, etc. Since much of the time these are stored in plain text on websites someone can gain access to many of your accounts by knowing these answers. Instead, put in mixed letters/numbers as answers and use a secure password manager to keep track of your answers. I came across this tip on Reddit. So I thought sharing it here would be helpful to someone.
Check The Password Complexity In Linux
There are plenty of tools and websites are available to test the password complexity. But, what we are going to discuss here is the easiest and effective method among them.
Install cracklib package if it is not installed already.
On Arch Linux and its derivatives, run:
On RHEL, Fedora, CentOS:
On Debian, Ubuntu, Linux Mint:
Now, It is time for some password complexity tests.
Let us start with a simple password.
Sample output:
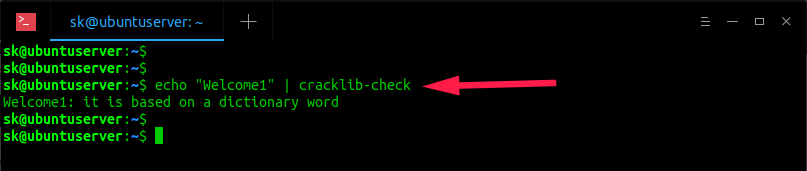
As you see in the above output, the given password is based on dictionary word, which is not recommended.
Let us see what will be the result if give a strong password.
Sample output:
Here is another one.
Sample output:
Great! These password are strong enough to use. Likewise, you can check the complexity of different passwords as described above.
Источник
HowTo: Linux Check Password Strength With Cracklib-check Command
U sing the same password on different servers allows attackers to access your accounts if cracker manage to steal your password from a less secure server. This is true for online website accounts too. So solution is to create unique passwords for server accounts like your email, sftp and ssh accounts. General guideline to create a strong and unique password is as follows:
Creating a strong and unique password for Linux or Unix-like systems
- Create a password with mix of numbers, special symbols, and alphabets.
- Make sure your password is hard to guess. You can use tool such as makepasswd to create hard to guess password.
- Do not use simple words like “password”, “123456”, “123abc” or “qwerty”.
- Use a unique password for all your server accounts.
- A minimum password length of 12 to 14 characters should be used. See how to configure CentOS / RHEL / Fedora Linux based server password quality requirements.
- Generating passwords randomly where feasible. You can do this with a simple shell script function.
- If possible use two-factor authentication.
- Use pam_crack to ensure strong passwords and to check passwords against a dictionary attack.
But, how do you test the effectiveness of a password in resisting guessing and brute-force attacks under Linux? The answer is simple use cracklib-check command.
Install cracklib on a Linux based system
Type the following yum command to install on RHEL and friends:
# yum install cracklib
Type the following apt-get command to install on Debian/Ubuntu and friends:
# apt-get install libcrack2
Say hello to cracklib-check
This command takes a list of passwords from keyboard (stdin) and checks them using libcrack2. The idea is simple: try to prevent users from choosing passwords that could be guessed by “crack” by filtering them out, at source.
Examples
Test a simple password like “password”, enter:
$ echo «password» | cracklib-check
Sample outputs:
Try sequential patterns such as “abc123456”:
$ echo «abc123456» | cracklib-check
Sample outputs:
Try a password with a mix of letters, numbers, and symbols:
$ echo ‘i1oVe|DiZza’ | cracklib-check
Sample outputs:
The above password increases the difficulty of guessing or cracking your password. I used a random phrase (easy to remember) “I Love Pizza” and inserted random characters to create a strong hard to guess password – “i1oVe|DiZza”.
Fig.01: Linux cracklib-check command examples
A note about security
The above examples all are insecure as passwords stored into your shell’s history file or displayed in ps command output. You can try following syntax:
Источник
Как проверить пароль в Linux?
Я хочу проверить в командной строке linux, совпадает ли заданный пароль открытого текста с зашифрованным паролем в / etc / shadow
(Мне нужно это для аутентификации пользователей сети. Я использую встроенный Linux.)
У меня есть доступ к самому файлу / etc / shadow.
Вы можете легко извлечь зашифрованный пароль с помощью awk. Затем вам нужно извлечь префикс $algorithm$salt$ (при условии, что в этой системе не используется традиционный DES, что сильно не рекомендуется, потому что в наши дни его можно перебрать).
Для проверки пароля базовая функция C есть crypt , но нет стандартной команды оболочки для доступа к ней.
В командной строке вы можете использовать однострочник Perl для вызова crypt пароля.
Так как это не может быть сделано в чисто инструментальных оболочках, если у вас есть доступный Perl, вы можете сделать все это в Perl. (Или Python, Ruby, . все, что у вас есть, которое может вызвать crypt функцию.) Предупреждение, непроверенный код.
На встроенной системе без Perl я бы использовал небольшую специализированную C-программу. Предупреждение, набранное прямо в браузере, я даже не пытался скомпилировать. Это предназначено для иллюстрации необходимых шагов, а не как надежная реализация!
Другой подход заключается в использовании существующей программы, такой как su или login . На самом деле, если вы можете, было бы идеально устроить так, чтобы веб-приложение могло выполнять все, что ему нужно su -c somecommand username . Трудность здесь заключается в том, чтобы ввести пароль su ; это требует терминала. Обычный инструмент для эмуляции терминала — ожидаемый , но это большая зависимость для встроенной системы. Кроме того, хотя он su находится в BusyBox, он часто опускается, поскольку для многих его применений требуется, чтобы двоичный файл BusyBox был установлен как root. Тем не менее, если вы можете сделать это, это самый надежный подход с точки зрения безопасности.
Посмотрите на man 5 shadow и man 3 crypt . Из последнего вы можете узнать, что хеши паролей /etc/shadow имеют следующую форму:
где id определяет тип шифрования и, читая далее, может быть одним из
В зависимости от типа хэша вам нужно использовать соответствующую функцию / инструмент для генерации и проверки пароля «вручную». Если система содержит mkpasswd программу, вы можете использовать ее, как предложено здесь . (Вы берете соль из файла теней, если это не было очевидно.) Например, с md5 паролями:
сгенерирует строку, которая должна соответствовать /etc/shadow записи.
Источник