- Cap to hccap windows
- pcap and cap dump file to hccapx — instantly
- Select and Upload your .(p)cap file:
- Output:
- Notes
- How to use?
- Explanation of the format
- Credits
- Popular
- Legal Notes
- Cap to hccap windows
- Converting Aircrack-ng Hashes to .hccapx Format and Cracking with Hashcat
- Downloading and Compiling the cap2hccapx Utility
- Converting the .cap File to .hccapx
- Cracking Considerations
- Cracking with Hashcat – Phone Numbers
- Cracking with Hashcat – Dictionary / Wordlists
- Cracking with Hashcat – Dictionary / Wordlist Modifications via Rules
- Conclusion
Cap to hccap windows
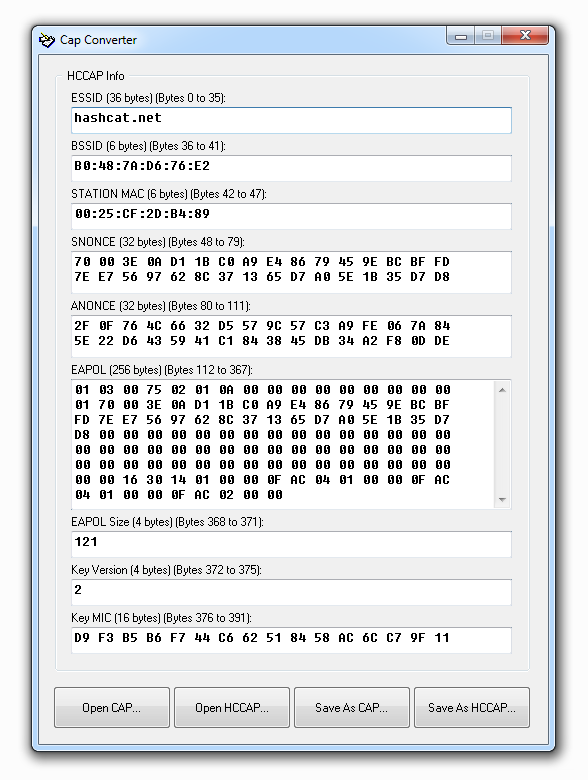
This is a small GUI tool for Windows that can open, edit and save WPA hash information from CAP and HCCAP files. It can.
- Convert CAP files to HCCAP files
- Convert HCCAP files back to CAP files
- Preview and edit the contents of an HCCAP file
It does not require any external programs or dependencies to be installed (such as Wireshark, WinPcap or libpcap). It directly reads and writes the raw bytes of the files.
Before converting it is recommended that you clean your caps first manually using Wireshark or with pyrit using the command.
pyrit -r INPUT.CAP -o OUTPUT.CAP strip
to only contain one handshake for one network but even if you don’t this program will still make it’s best attempt at extracting the correct WPA handshake information.
How to Convert CAP to HCCAP
- Press the «Open CAP. » button to open a .CAP file
- Verify the hash information looks correct in the «HCCAP Info» box
- Press the «Save As HCCAP. » button to save the information to an .HCCAP file
How to Convert HCCAP to CAP
- Press the «Open HCCAP. » button to open a .HCCAP file
- Verify the hash information looks correct in the «HCCAP Info» box
- Press the «Save As CAP. » button to save the information to a .CAP file
Background
Cracking WPA/WPA2 with oclHashcat requires the use of an HCCAP file which is a custom file format designed specifically for hashcat. Typically this file is created using aircrack-ng (v1.2-beta1 or later) using the command.
aircrack-ng -J HCCAP_FILE CAP_FILE.CAP
or by using this online converter (which is powered by cap2hccap). However if you aren’t comfortable with either of those options this program allows you to perform your CAP-to-HCCAP conversions offline with a familiar Windows interface.
This program effectively merges together the functionality and adds a GUI to these existing projects:
VB6 Runtimes
This program was written in Visual Basic 6 which means it should work on any modern version of Windows but just in case you need to download the VB6 runtimes you can do so from here:
pcap and cap dump file to hccapx — instantly
Select and Upload your .(p)cap file:
Output:
Notes
- Uploaded files (.cap) will be deleted immediately. We do NOT store your .cap files
- Converted files (.hccapx) will be stored for 2 days before being deleted
- This site is using the best-in-class tool hcxtools to convert cap files
- The goal of this page is to make it very easy to convert .cap files to .hccapx
- We also offer a service to try to recover the WPA password, just upload your file (.cap or .hccapx) here.
- See also cap to hash converter.
How to use?
More than easy, just select and upload your .(p)cap file. If valid, the file will be converted into a .hccapx file, which is readable by Hashcat.
Explanation of the format
hccapx is a custom format, specifically developed for Hashcat, to be used for hash type -m 2500 = WPA/WPA2
An exhaustive description of this custom format can be found on their official wiki.
Credits
Credits go to hcxtools project
Online Hash Crack is an online service that attempts to recover your lost passwords:
— Hashes (e.g. MD5, NTLM, WordPress. )
— Wifi WPA handshakes
— Office encrypted files (Word, Excel. )
— Apple iTunes Backup
— ZIP / RAR / 7-zip Archive
— PDF documents
Popular
Legal Notes
By using our service you agree that you are not violating any laws or regulations on copyright or privacy issues that exist in your country. Terms & Conditions
Cap to hccap windows
This is a small GUI tool for Windows that can open, edit and save WPA hash information from CAP and HCCAP files. It can.
- Convert CAP files to HCCAP files
- Convert HCCAP files back to CAP files
- Preview and edit the contents of an HCCAP file
It does not require any external programs or dependencies to be installed (such as Wireshark, WinPcap or libpcap). It directly reads and writes the raw bytes of the files.
Before converting it is recommended that you clean your caps first manually using Wireshark or with pyrit using the command.
pyrit -r INPUT.CAP -o OUTPUT.CAP strip
to only contain one handshake for one network but even if you don’t this program will still make it’s best attempt at extracting the correct WPA handshake information.
How to Convert CAP to HCCAP
- Press the «Open CAP. » button to open a .CAP file
- Verify the hash information looks correct in the «HCCAP Info» box
- Press the «Save As HCCAP. » button to save the information to an .HCCAP file
How to Convert HCCAP to CAP
- Press the «Open HCCAP. » button to open a .HCCAP file
- Verify the hash information looks correct in the «HCCAP Info» box
- Press the «Save As CAP. » button to save the information to a .CAP file
Background
Cracking WPA/WPA2 with oclHashcat requires the use of an HCCAP file which is a custom file format designed specifically for hashcat. Typically this file is created using aircrack-ng (v1.2-beta1 or later) using the command.
aircrack-ng -J HCCAP_FILE CAP_FILE.CAP
or by using this online converter (which is powered by cap2hccap). However if you aren’t comfortable with either of those options this program allows you to perform your CAP-to-HCCAP conversions offline with a familiar Windows interface.
This program effectively merges together the functionality and adds a GUI to these existing projects:
VB6 Runtimes
This program was written in Visual Basic 6 which means it should work on any modern version of Windows but just in case you need to download the VB6 runtimes you can do so from here:
Converting Aircrack-ng Hashes to .hccapx Format and Cracking with Hashcat
In the previous two articles in this series I covered how to set up an external USB Wi-Fi adapter and put it in to monitor mode, and talked about how to capture a WPA2-PSK handshake for the purposes of taking it offline to crack. If you missed either of those articles, please go check them out.
Downloading and Compiling the cap2hccapx Utility
Somewhat recently, Hashcat was updated and now doesn’t get along with .cap files. Hashcat prefers those files be converted over to its own format, which ends in .hccapx. They have released an open source utility for this, but it’s not downloadable in a pre-compiled form. Not to worry. Compiling it in Kali Linux is a single command, and Kali already has a C compiler installed by default (gcc). Once the file is converted to .hccapx, you can use Hashcat on your Kali machine to crack the file, or if you have a Windows gaming rig with a GPU or two in it, fear not… Hashcat is available for Windows as well and you can just as easily crack it there.
The first thing you’ll want to do is get a copy of the cap2hccapx.c source code. The simplest way is to open a shell on Kali, change directories to your home directory (if you aren’t there already), and get the file via the wget command.
At the time of this writing, that’s where the file is located. I’ll host a copy of the file for archive purposes in case the above file disappears.
Whichever way you’re able to grab it, you can compile the file with the following command.
That’s it. An executable file called cap2hccapx will be created. The easiest way I’ve found to use this is to move that file to the /bin directory. That way you can use the command no matter where you are in the Linx filesystem, since /bin is already in the system path. Doing that is simple enough with one command. You can also get rid of the source, since we won’t need it anymore.
Optionally, you can go online and use the online tool provided at https://hashcat.net/cap2hccapx/ to convert cap files to hccapx files, but for some reason I couldn’t get this to work. Plus, compiling your own binary and being able to do it all locally from the command line is so much more satisfying anyway.
You’ll only have to do this once, and once the cap2hccapx binary is in your /bin directory, you’ll be able to use it indefinitely. To check and make sure that it’s working properly, you can attempt to execute it from the command line while in any working directory by running “cap2hccapx.” You should get the following output.
Converting the .cap File to .hccapx
Converting the .cap file to .hccapx is a quick and dirty single-command affair. I’ll be using the filename from the previous example in my syntax here, so obviously you’ll want to change the syntax if your capture filename is different.
This command will produce a file called, in this instance, capturefile-01.hccapx. Great. That was easy, no?
Cracking Considerations
At the end of the last article I talked a little about the importance of using GPUs while attempting to brute force hashes. It blew my mind how much faster my GTX 1070 was able to complete a 10,000,000 word dictionary attack on a hash in 52 seconds, when the same operation on a 3.0 Ghz Core i5 took 8 hours and 14 minutes. The largest GPU you can get your hands on, the better.
At this point in the process, we need to make a decision as to what to do with our .hccapx file. Do we keep it here on our Kali machine / VM and attempt to crack it here? If you’re running Kali in a VM, I would strongly advise against this. Similarly, if you’re running on a smaller Kali box like a GPD Pocket or a Raspberry Pi, don’t even think about it. If the fastest CPU you have is on your dedicated Kali machine, then that’s the only option you may have, but if you have a machine with a dedicated GPU, that’d be best.
I understand that many people don’t run Kali on their “main rig,” in fact, Kali tells you not to, since Kali is designed to be used by the root user almost exclusively. A common scenario is that one typically has a machine dedicated to Kali, and another machine (which is usually less portable, and thusly would contain a GPU) that either runs Windows (gaming) or another distribution of Linux. Because of this, I’ll provide syntax for cracking via Hashcat on both Windows and Linux. Don’t worry though – they’re very similar, so if you learn one, you’ll basically know the other.
Cracking with Hashcat – Phone Numbers
Hashcat is a great utility that’s very easy to use and gives you a ton of options. There’s so much syntax that can be used with Hashcat that it’s impossible to go over all of it here. As a result, I’ll simply go over the techniques that I use the most. Since this series of articles has been about cracking WPA2 pre-shared keys, I’ll keep the focus narrowed to cracking just those in order to keep the article concise.
When cracking a WPA2 pre-shared key, the first thing that I like to start with is running through 10-digit phone numbers. I’ve seen studies that show as many as 60% of WPA2 pre-shared keys in the US are 10-digit phone numbers (area code and then the 7-digit number). People do this because it’s easy for them to remember, and long enough to satisfy the 8-character minimum required for WPA2 pre-shared keys.
Running through absolutely every 10-digit number combination would require you to try 10,000,000,000 possible combinations. That would take quite a long time. Think about it though – if the AP is local, there might only be 3 or 4 area codes around. It’d be a much more efficient use of time to crack using the known area codes. If we did that, and say used 555 as our area code, the number of combinations would be reduced from 10,000,000,000 to 1,000,000. From my experience, a GeForce GTX 1070 can do that in under a minute. Not bad for every possible phone number combination in an area code.
The syntax would be as follows. Note that this is the Windows command. The Linux command would be identical, simply remove the “64” after the word hashcat.
This may look confusing at first, but let’s break it down by argument.
-m 2500 tells hashcat that we are trying to attack a WPA2 pre-shared key as the hash type. Hashcat has a bunch of pre-defined hash types that are all designated a number. You can use the –help switch to get a list of these different types, but for now we’re doing WPA2 so we’ll use 2500.
-a 3 sets the attack mode and tells hashcat that we are brute forcing our attempts. A list of the other attack modes can be found using the –help switch.
-l ?d specifies that we are going to use a custom character set for our brute force attempt. Our custom character set is defined by what’s after the ?. In this case we’re using ?d, which means “use only digits” (0-9). Other options here would be ?l for letters (uppercase and lowercase) and ?s for special characters. The -1 indicates that this it the first custom character set that we are defining in this command. More can be created with -2, -3, etc.
-o cracked is used to specify an output file called simply “cracked” that will contain the WPA2 pre-shared key in plain text once the crack happens successfully.
capturefile-01.hccapx is the name of our capture file containing the handshake. Note that if you try to use a .cap file here, it won’t work, which is why we converted it earlier.
555?1?1?1?1?1?1?1 is where the magic happens. This is our mask, which tells hashcat what we want to do with our custom-defined character set. Notice that in our mask we specify the first 3 digits of our phone number (555). The next 7 digits reference our custom character set as defined above with the -1 switch. Remember that we defined our custom set with digits only (0-9), so this command is telling hashcat that we want to use a 0-9 digit for every ?1 in the mask. This effectively tells hashcat that we want to brute force 555xxxxxxx where x is a digit 0-9. Make sense?
Using the above template you should be able to replace “555” with local area codes, and given a fast GPU, run through all possible combination in a number of minutes.
Cracking with Hashcat – Dictionary / Wordlists
If the phone number approach doesn’t work, and a lot of times it won’t, your next best bet is a dictionary attack. You can find several dictionaries, also sometimes called wordlists or password lists, online. Kali comes with quite a few good ones, which are located in /usr/share/wordlists. The best, and largest of this, is called rockyou.txt and is fairly large. That particular wordlist comes zipped on a standard install, so you’ll have to unzip it with the gunzip command.
If you want additional wordlists, finding them online is very easy. A quick Google search of “wpa2 ask wordlists” returns 53,000 results, and even on the first page of results I’m seeing wordlists up to 13GB in size that are compiled from years of previous experience gleaned from leaks and dumps of known passwords.
Once you’ve picked out a wordlist that you’d like to use, running all of the passwords in that wordlist against our hccapx file is a single command.
Again, this is the Windows syntax, so for Linux just remove the “64”. This syntax assumes that your wordlist is called wordlist.lst, that your capture file is called capturefile-01.hccapx, and that both of those files are in your current working directory.
Another syntax example for this command would be as follows if we were in Linux and using the rockyou.txt wordlist.
Gathering wordlists and seeing which ones produce great results is more a matter of luck than anything. Hunting and gathering will eventually provide you with a collection of wordlists, and you’ll eventually have quite a collection of wordlists.
Cracking with Hashcat – Dictionary / Wordlist Modifications via Rules
Because this article is getting long, I’ll keep this section somewhat short. Hashcat has a built-in function for writing custom scripts for modifying each line in a wordlist automatically. For example, say you have a wordlist with only the word “password” in it. Running a rule against this file might make hashcat first try “password,” then try “password1,” then “password123,” etc. The variations are dependent on the rules written in the rules file.
Luckily, you don’t have to be a master at writing rules files in order to utilize them. Like wordlists, Kali comes with a bunch of rules that are built in. The most famous one of these has 64 different modifier variations built in and is called base64.rule. The Windows syntax for this rule is as follows.
Again, mind the syntax. This assumes that the base64.rule file is in a subdirectory called rules, and the capturefile-01.hccapx file and rockyou.txt file are in the working directory. Relative and absolute paths can be used in either Linux or Windows for any of these parameters. Also keep in mind that if you are applying 64 variations to each password in the list, that running this command with the rule applied that applies base64.rule is going to take 64 times longer than just running the wordlist alone.
Conclusion
As you can see, hashcat is a very powerful tool. Cracking password is sometimes more luck than skill, depending on what you already know about the password, or if you have to rely on a wordlist.
Remember old-school techniques as well. Shoulder surfing can be your friend here. If you see someone enter a password and only grab the first 3 or 4 characters, those are characters that can be eliminated and you can use a directed attack with custom character sets applied much like we did with the phone number example above.
If you enjoyed this tutorial and would like to see more, please feel free to share this article on social media, comment below letting me know what else you’d like to see, and follow me on Twitter @JROlmstead.