- Window manager
- Contents
- Overview
- Диспетчер пакетов Windows (предварительная версия) Windows Package Manager (preview)
- Диспетчер пакетов Windows для разработчиков Windows Package Manager for developers
- Диспетчер пакетов Windows для независимых поставщиков программного обеспечения Windows Package Manager for ISVs
- Основные сведения о диспетчерах пакетов Understanding package managers
- Information about the Attachment Manager in Microsoft Windows
- Summary
- Introduction
- Workarounds when you cannot download a file or a program
- Configuring the Attachment Manager
- Hide mechanisms to remove zone information
- More Information
Window manager
A window manager (WM) is system software that controls the placement and appearance of windows within a windowing system in a graphical user interface (GUI). It can be part of a desktop environment (DE) or be used standalone.
Contents
Overview
Window managers are X clients that control the appearance and behaviour of the frames («windows») where the various graphical applications are drawn. They determine the border, title bar, size, and ability to resize windows, and often provide other functionality such as reserved areas for sticking dockapps like Window Maker, or the ability to tab windows like Fluxbox. Some window managers are even bundled with simple utilities like menus to start programs or to configure the WM itself.
The Extended Window Manager Hints specification is used to allow window managers to interact in standard ways with the server and the other clients.
Some window managers are developed as part of a more comprehensive desktop environment, usually allowing the other provided applications to better interact with each other, giving a more consistent experience to the user, complete with features like desktop icons, fonts, toolbars, wallpapers, or desktop widgets.
Other window managers are instead designed to be used standalone, giving the user complete freedom over the choice of the other applications to be used. This allows the user to create a more lightweight and customized environment, tailored to their own specific needs. «Extras» like desktop icons, toolbars, wallpapers, or desktop widgets, if needed, will have to be added with additional dedicated applications.
Some standalone WMs can be also used to replace the default WM of a DE, just like some DE-oriented WMs can be used standalone too.
Prior to installing a window manager, a functional X server installation is required. See Xorg for detailed information.
Диспетчер пакетов Windows (предварительная версия) Windows Package Manager (preview)
Сейчас предоставляется общедоступная предварительная версия Диспетчера пакетов Windows и средства winget. Перед выпуском общедоступной версии в решения могут быть внесены значительные изменения. Windows Package Manager and the winget tool are in public preview and may be substantially modified before they are generally available. Майкрософт не дает никаких гарантий, явных или подразумеваемых, в отношении предоставленной здесь информации. Microsoft makes no warranties, express or implied, with respect to the information provided here.
Диспетчер пакетов Windows — это комплексное решение для управления пакетами, которое состоит из программы командной строки и набора служб для установки приложений в Windows 10. Windows Package Manager is a comprehensive package manager solution that consists of a command line tool and set of services for installing applications on Windows 10.
Диспетчер пакетов Windows для разработчиков Windows Package Manager for developers
Разработчики используют программу командной строки winget для обнаружения, установки, обновления, удаления и настройки проверенного набора приложений. Developers use the winget command line tool to discover, install, upgrade, remove and configure a curated set of applications. После установки разработчики могут получить доступ к winget с помощью терминала Windows, PowerShell или командной строки. After it is installed, developers can access winget via the Windows Terminal, PowerShell, or the Command Prompt.
Диспетчер пакетов Windows для независимых поставщиков программного обеспечения Windows Package Manager for ISVs
Независимые поставщики программного обеспечения могут использовать Диспетчер пакетов Windows в качестве канала распространения пакетов программного обеспечения, содержащих их средства и приложения. Independent Software Vendors (ISVs) can use Windows Package Manager as a distribution channel for software packages containing their tools and applications. Для отправки пакетов программного обеспечения (содержащих установщики MSIX, MSI или EXE) в Диспетчер пакетов Windows мы предоставляем на сайте GitHub репозиторий манифестов пакетов сообщества Майкрософт с открытым исходным кодом. Независимые поставщики программного обеспечения могут передавать в него манифесты пакетов, которые затем могут быть включены в Диспетчер пакетов Windows. To submit software packages (containing .msix, .msi, or .exe installers) to Windows Package Manager, we provide the open source Microsoft Community Package Manifest Repository on GitHub where ISVs can upload package manifests to have their software packages considered for inclusion with Windows Package Manager. Манифесты проверяются автоматически, однако они также могут просматриваться вручную. Manifests are automatically validated and may also be reviewed manually.
Основные сведения о диспетчерах пакетов Understanding package managers
Диспетчер пакетов — это система или набор средств, используемых для автоматизации установки, обновления, настройки и использования программного обеспечения. A package manager is a system or set of tools used to automate installing, upgrading, configuring and using software. Большинство диспетчеров пакетов предназначены для обнаружения и установки средств для разработчиков. Most package managers are designed for discovering and installing developer tools.
В идеале разработчики используют диспетчер пакетов, чтобы задать компоненты, необходимых им для разработки решений под конкретный проект. Ideally, developers use a package manager to specify the prerequisites for the tools they need to develop solutions for a given project. Затем диспетчер пакетов выполняет декларативные инструкции по установке и настройке средств. The package manager then follows the declarative instructions to install and configure the tools. Диспетчер пакетов сокращает время, затрачиваемое на подготовку среды, и помогает обеспечить установку на компьютеры одних и тех же версий пакетов. The package manager reduces the time spent getting an environment ready, and it helps ensure the same versions of packages are installed on their machine.
Диспетчеры пакетов сторонних разработчиков могут использовать репозиторий манифестов пакетов сообщества Майкрософт для пополнения своего каталога программного обеспечения. Third party package managers can leverage the Microsoft Community Package Manifest Repository to increase the size of their software catalog.
Information about the Attachment Manager in Microsoft Windows
Summary
This article describes Attachment Manager in Windows. This article includes the methods to configure Attachment Manager and the workarounds for two issue with Attachment Manager.
Introduction
The Attachment Manager is included in Microsoft Windows to help protect your computer from unsafe attachments that you might receive with an e-mail message and from unsafe files that you might save from the Internet.
If the Attachment Manager identifies an attachment that might be unsafe, the Attachment Manager prevents you from opening the file, or it warns you before you open the file. For more information about Attachment Manager, go to the «More Information» section.
Workarounds when you cannot download a file or a program
Many people encounter issues when they try to download a file or a program from the Internet. This could be caused by a number of reasons. Here we provide two general solutions for you to try if you are getting an error that your download is blocked, or if you get «virus scan failed» or «virus detected» messages.
You cannot download any file if the «File download» option is disabled in the Internet security settings. Follow these steps to check the Internet security settings:
Start the Internet Properties window.
Windows 7
Click Start, click All Programs, and then open the Accessories folder.
Type inetcpl.cpl, and then click OK.
Windows 8 or 10
From the Start screen, type inetcpl.cpl, and then press Enter.
In the Internet Properties window, click the Security tab, click the Ineternet zone (globe icon), and then click the Custom level button.
In the Security Settings window, scroll down to Downloads > File download.
Click to select Enable.
Scroll down the list further to Miscellaneous > Launching applications and unsafe files.
Click to select Prompt (recommended).
You may receive a «Virus scan failed» or «Virus detected» error message when you try to open or save a file or a program from Internet. In most cases, it is not caused by the Windows operating system, but by the antivirus software. If you are certain that the source you are trying to open is safe and trusted, try the following workaround to disable the virus scanning temporarily, and then enable the virus scanning immediately after you complete downloading the program or file. You have to be very cautious about using this workaround. Otherwise, you may be exposed to virus attacks.
Start Registry Editor.
Windows 7
Click Start, click All Programs, and then open the Accessories folder.
Type regedit.exe, and then click OK.
Windows 8 or 10
From the Start screen, type regedit.exe, and then press Enter.
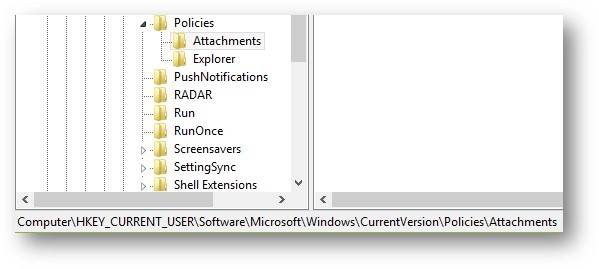
Locate the following registry subkeys: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments
If you do not see the Attachments subkey, create it by right clicking Policies, select New, click Key, and then type Attachments as the key name.
Right click Attachments, select New, and then click DWORD (32-bit) Value.
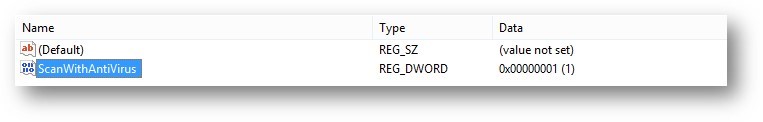
Type ScanWithAntiVirus as the value name, and then press Enter.
Right-click the new ScanWithAntiVirus DWORD value, and then click Modify.
In the Value data box, type 1, and then click OK.
Exit Registry Editor.
Log off and log in Windows to make the change take effect.
Open or save the program or file that you failed before.
Note We suggest you change the value of ScanWithAntiVirus subkey to 3 to enable the virus scan right after you completely open or save the program or file.
Configuring the Attachment Manager
There are several features of the Attachment Manager that can be configured by using Group Policy or the local registry.
This policy setting lets you manage the default risk level for file types. To fully customize the risk level for file attachments, you may also have to configure the trust logic for file attachments:
High Risk
If the attachment is in the list of high risk file types and is from the restricted zone, Windows blocks the user from accessing the file. If the file is from the Internet zone, Windows prompts the user before accessing the file.
Moderate Risk
If the attachment is in the list of Moderate Risk file types, Windows will not prompt the user before accessing the file, regardless of the file’s zone information.
Low Risk
If the attachment is in the list of low risk file types, Windows will not prompt the user before accessing the file, regardless of the file’s zone information.
If you enable this policy setting, you can specify the default risk level for file types. If you disable this policy setting, Windows sets the default risk level to moderate. If you do not configure this policy setting, Windows sets the default risk level to moderate.
User Configuration\Administrative Templates\Windows Components\Attachment Manager
High (6150)
or
Moderate (6151)
or
Note The default value of the DefaultFileTypeRisk registry entry is Moderate (6151).
This policy setting lets you manage whether Windows marks file attachments that have information about their zone of origin. These zones or origin are Internet, intranet, and local. This policy setting requires the NTFS file system to function correctly and will fail without notice on systems that use FAT32. By not preserving the zone information, Windows cannot make appropriate risks assessments. If you enable this policy setting, Windows does not mark file attachments by using their zone information. If you disable this policy setting, Windows marks file attachments by using their zone information. If you do not configure this policy setting, Windows marks file attachments by using their zone information.
User Configuration\Administrative Templates\Windows Components\Attachment Manager
Note The default value of the DefaultFileTypeRisk registry entry is Off (2).
Hide mechanisms to remove zone information
This policy setting lets you manage whether users can manually remove the zone information from saved file attachments by clicking
Unblock on the file’s Properties tab or by clicking to select a check box in the Security Warning dialog box. Removing the zone information lets users open potentially dangerous file attachments that Windows has blocked users from opening. If you enable this policy setting, Windows hides the check box and the Unblock button. If you disable this policy setting, Windows shows the check box and the Unblock button. If you do not configure this policy setting, Windows shows the check box and the Unblock button.
User Configuration\Administrative Templates\Windows Components\Attachment Manager
Note The default value of the DefaultFileTypeRisk registry entry is Off (0).
These policy settings let you configure the list of low, moderate, and high risk file types. The High list takes precedence over the Moderate and Low risk inclusion lists. Also, an extension is listed in more than one inclusion list. If you enable this policy setting you can create a custom list of low, moderate, and high risk file types. If you disable this policy setting, Windows uses its built in list of file types. If you do not configure this policy setting, Windows uses its built in list of file types.
User Configuration\Administrative Templates\Windows Components\Attachment Manager
HighRiskFileTypes
ModRiskFileTypes
LowRiskFileTypes
This policy setting lets you configure the logic that Windows uses to determine the risk for file attachments. Preferring the file handler instructs Windows to use the file handler data over the file type data. For example, it instructs Windows to trust Notepad.exe, but do not trust .txt files. Preferring the file type instructs Windows to use the file type data over the file handler data. For example, trust .txt files, regardless of the file handler. Using both the file handler and type data is the most restrictive option. Windows chooses the more restrictive recommendation. This causes users to see more trust prompts than selecting the other options. If you enable this policy setting, you can select the order in which Windows processes risk assessment data. If you disable this policy, Windows uses its default trust logic which prefers the file handler over the file type.
User Configuration\Administrative Templates\Windows Components\Attachment Manager
File Type (1)
or
Handler (2)
or
Both (3)
Note The default value of the DefaultFileTypeRisk registry entry is Handler (2).
This policy setting lets you manage the behavior for notifying registered antivirus programs. If multiple programs are registered, they will all be notified. If the registered antivirus program already performs on-access checks or scans files as they arrive on the computer’s e-mail server, additional calls would be redundant. If you enable this policy, Windows tells the registered antivirus program to scan the file when a user opens a file attachment. If the antivirus program fails, the attachment is blocked from being opened. If you disable this policy, Windows does not call the registered antivirus programs when file attachments are opened. If you do not configure this policy, Windows does not call the registered antivirus programs when file attachments are opened.
User Configuration\Administrative Templates\Windows Components\Attachment Manager
Off (1)
or Optional (2) or
Note The default value of the DefaultFileTypeRisk registry entry is Off (1). When the value is set to Optional (2), all scanners are called even after one reports a detection.
For more information, click the following article number to view the article in the Microsoft Knowledge Base:
182569 Internet Explorer security zones registry entries for advanced users
More Information
The following determine whether you are prevented from opening the file or whether you are warned before you open the file:
The type of program that you are using.
The file type that you are downloading or trying to open.
The security settings of the Web content zone that you are downloading the file from.
Note You can configure the Web content zones in Microsoft Internet Explorer on the Security tab. To view the Web content zones, click Tools, click Internet Options, and then click the Security tab. The following are the four Web content zones:
The Attachment Manager uses the IAttachmentExecute application programming interface (API) to find the file type, to find the file association, and to determine the most appropriate action.
Microsoft Outlook Express and Microsoft Internet Explorer use the Attachment Manager to handle e-mail attachments and Internet downloads.
The Attachment Manager classifies files that you receive or that you download based on the file type and the file name extension. Attachment Manager classifies files types as high risk, medium risk, and low risk. When you save files to your hard disk from a program that uses the Attachment Manager, the Web content zone information for the file is also saved with the file. For example, if you save a compressed file (.zip) that is attached to an e-mail message to your hard disk, the Web content zone information is also saved when you save the compressed file. When you try to extract the contents from the compressed file, or if you try to run a file, you cannot. The Web content zone information is saved together with the files only if the hard disk uses the NTFS file system.
You can open a blocked file from a known source if you want to. To open a blocked file, follow these steps:
Right-click the blocked file, and then click
Properties.
In the General tab, click
Unblock.
When you try to download or open a file from a Web site that is in the restricted Web content zone, you may receive a message that indicates that the file is blocked.
When you try to open high-risk file types from sites that belong to the Internet Web content zone, you may receive a warning message, but you may be able to open these types of files.
The file types that the Attachment Manager labels as high-risk include the following: